
Chief Research Officer
Block Public Approval Access Exploit with CUBE3.AI
While training CUBE3.AI machine learning models, I noticed a preventable theft that could have secured $21K USDT, if the developers had integrated our products. The public approval access exploit began on July 14th, at approximately 6pm UTC, and the community was alerted July 15th post exploit (about 12 hours later).
At CUBE3.AI, we are working to not only decrease the time to detect smart contract vulnerabilities but more importantly, block exploits through our Runtime Application Self-Protection (RASP) “Protect” product. My co-founder and CUBE3 CEO, Einaras Gravrock, previously outlined the web3 security gap here.
Protecting Web3 with CUBE3.AI
First, a quick overview on how our team at CUBE3.AI can help protect smart contracts for developers, companies, and communities. At CUBE3, whenever a new contract is verified on-chain, CUBE3 scans for exploits, vulnerabilities and compliance risk through our Detect product. If problems are detected, we tag the new contract address, so the world can be notified of any threats. If a customer integrates CUBE3 Protect, any malicious transactions are blocked from executing on-chain. This is a deterministic rather than probabilistic security advantage we provide our customers.
We monitor for clients and partners, so we can block transactions before they occur. We are providing our Detect and Manage products free of charge as a public good for the community once we launch. Our partners and clients already have early access to these tools.
Sign up here, so you can get access the moment we launch in August.
Don’t Let Access Control Vulnerabilities Exploit Your Contract
In summary, this public approval vulnerability (a type of access control vulnerability) was detected by a malicious actor, they deployed a contract to drain the wallet, and waited 12 hours until they executed their exploit to inflict maximum damage.
Public Approval Exploit Timeline:
1) 2023-07-11 12:53:59 UTC = USDTStakingContract28 (vulnerable) contract deployed.
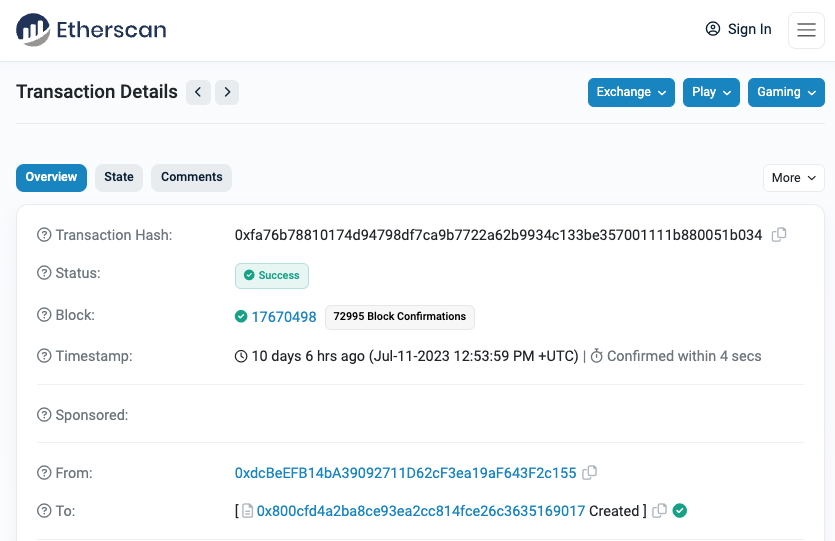
- Contract: 0x800cfD4A2ba8CE93eA2cc814Fce26c3635169017
- Deployer: 0xdcBeEFB14bA39092711D62cF3ea19aF643F2c155
<!-- NOTE: The vulnerability with USDTStakingContract28 source code can be found at line 152 -->
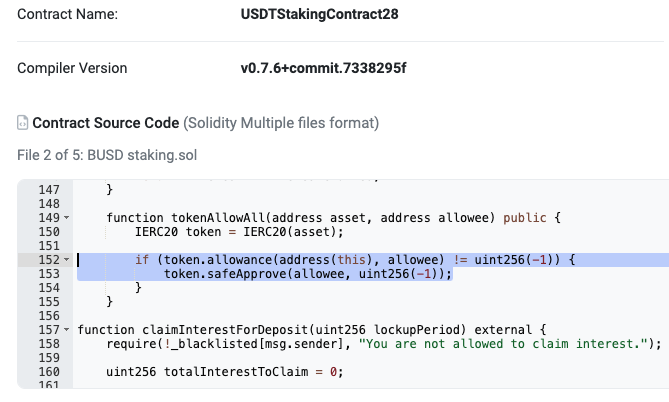
2) 2023-07-14 17:23:23 UTC = Contract funded with $500 USDT.
<!-- NOTE: This could be a threshold trigger for malicious actors to investigate a contract for exploitation. -->
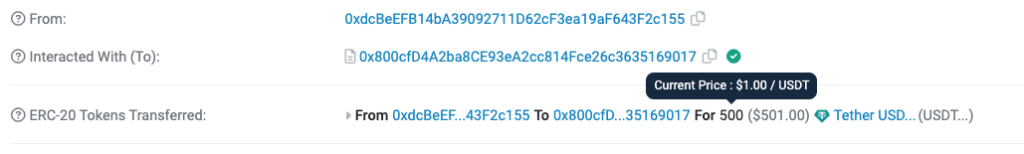
3) 2023-07-14 18:43:59 = Attacker deploys their contract.
- Contract: 0xb754EBdBa9B009113b4cF445a7cb0FC9227648aD
- Deployer: 0x000000915F1B10B0EF5c4EFE696Ab65f13F36E74
<!-- NOTE: If the victim/developer(s) had integrated CUBE3.AI, they could have been alerted this contract was fraudulent. CUBE3 flagged the contract as Unsafe in the Fraud category with a Risk Score of 80 -->
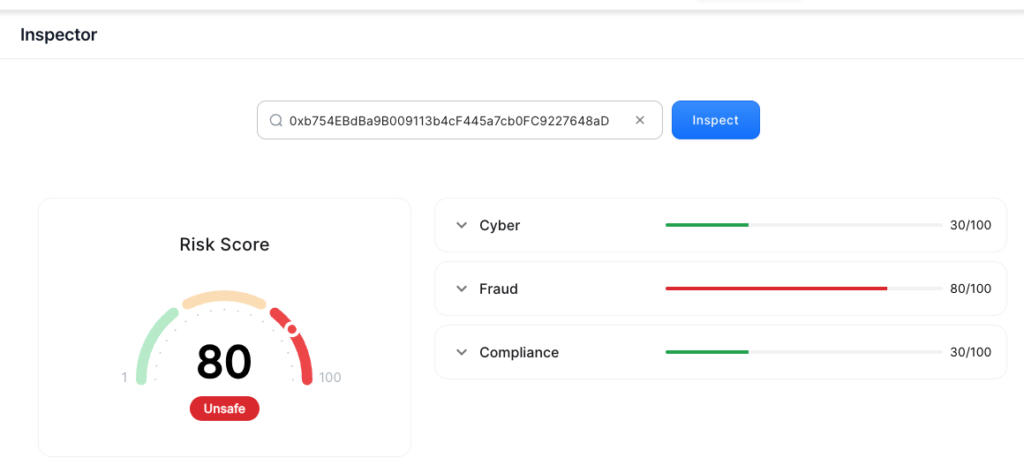
At this point, the malicious actor could have drained the wallet, but didn’t. They were patient, either expecting or hoping the sum would increase. Unfortunately, the story continues…
4) 2023-07-15 4:54:35 = Victim sends money to the contract to get interest (0x3c = 60 days)
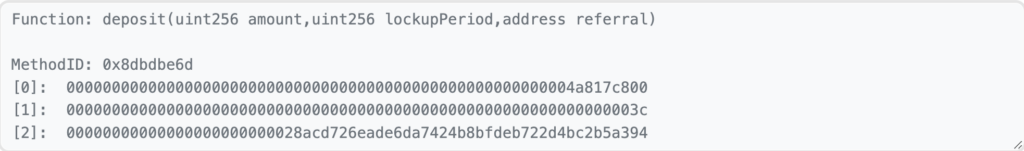
5) 2023-07-15 4:54:59 = Attacker stole the money with pre-deployed contract 24 seconds after victim’s deposit.
- 3 blocks after the original transaction, over 20K is stolen with the previously deployed malicious contract
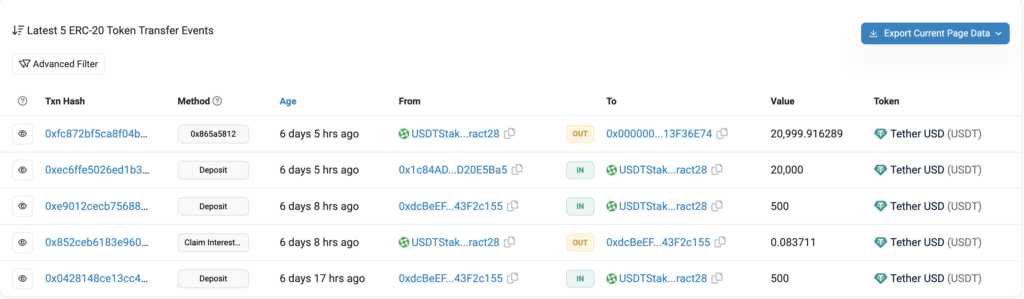
6) 2023-07-15 7:07:00 After the incident, PeckShield does a service for the community and alerts of the vulnerability and fraudulent transaction addresses.
Block Smart Contract Access Control Vulnerability with CUBE3.AI
Due to a public approval vulnerability in USDTStakingContract28, a malicious actor was able to execute an attack a day later. This would have been prevented if the malicious contract was tagged with CUBE3.AI’s out-of-the-box RASP solution. CUBE3 can help protect smart contracts by scanning for exploits, vulnerabilities, and compliance risks, and blocking malicious transactions from going on-chain. We encourage members of the web3 community to sign up to gain the benefits of CUBE3.AI’s solution and protect your smart contracts with real-time transaction security.
Join our Telegram and follow us for more updates.
Give us feedback on what features will help you secure web3.

 Tamás Kelemen
Tamás Kelemen
 Einaras Gravrock
Einaras Gravrock

 Sarunas Matulevicius
Sarunas Matulevicius

 Attila Marosi-Bauer
Attila Marosi-Bauer
 CUBE3.AI
CUBE3.AI





















