
Chief Research Officer
How to Preemptively Detect Rug Pull Scams Worth Millions with CUBE3.AI
In the past few days, CUBE3.AI detected criminals perpetrating multiple rug pull scams totaling over $17 million in market cap (at time of writing). We are sharing their addresses and tactics in order to protect the wider ecosystem.
The scam campaigns operate on multiple fronts simultaneously; primarily orchestrated from this address:
0x26ea753bb840f691c87656a01e85eca1854b7a6c
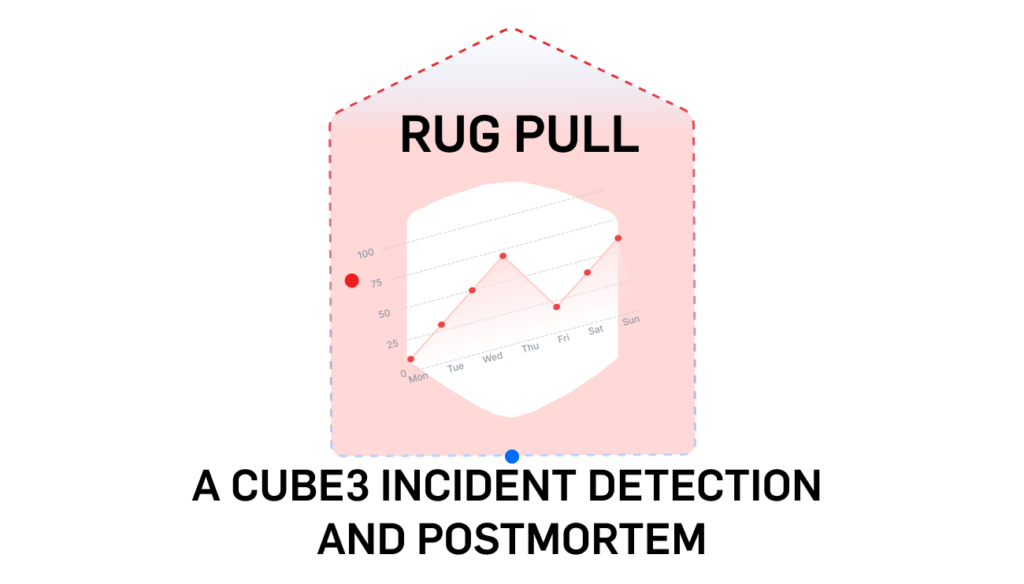
Although the latest campaign was through a token called INTRO, the perpetrators behind this scheme repetitively carry out similar fraudulent activities daily, over prolonged periods.
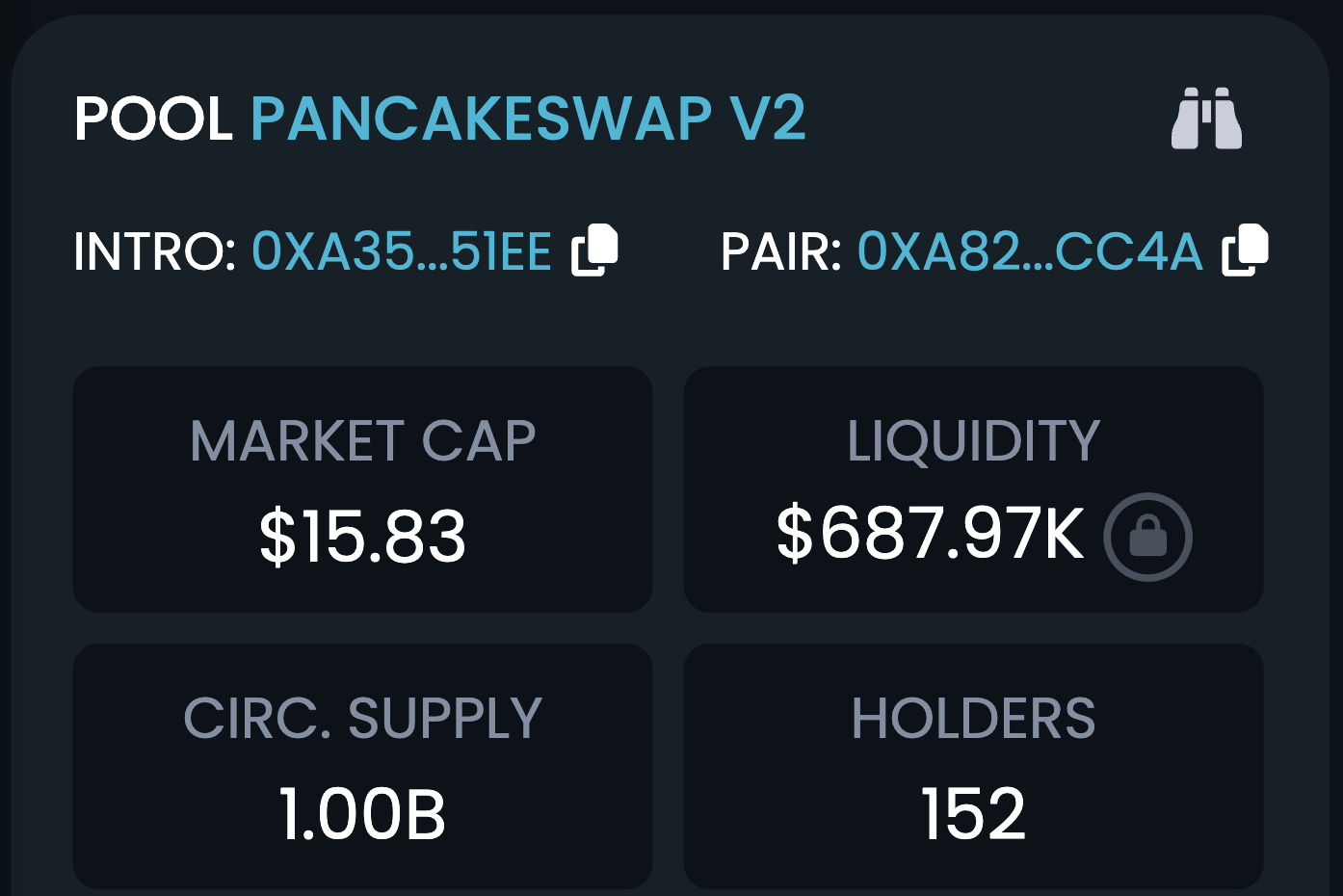
According to data from BscScan, this address creates multiple tokens and performs multiple rug pulls and has been involved in tens of thousands of transfer transactions. Here is the current market cap of INTRO at the time of writing:
The Rug Pull Strategy
The strategy is straightforward, yet deceptive:
1) Deploy tokens.
2) Create one (or several) trading pools (markets) for the tokens.
3) Generate buzz around token.
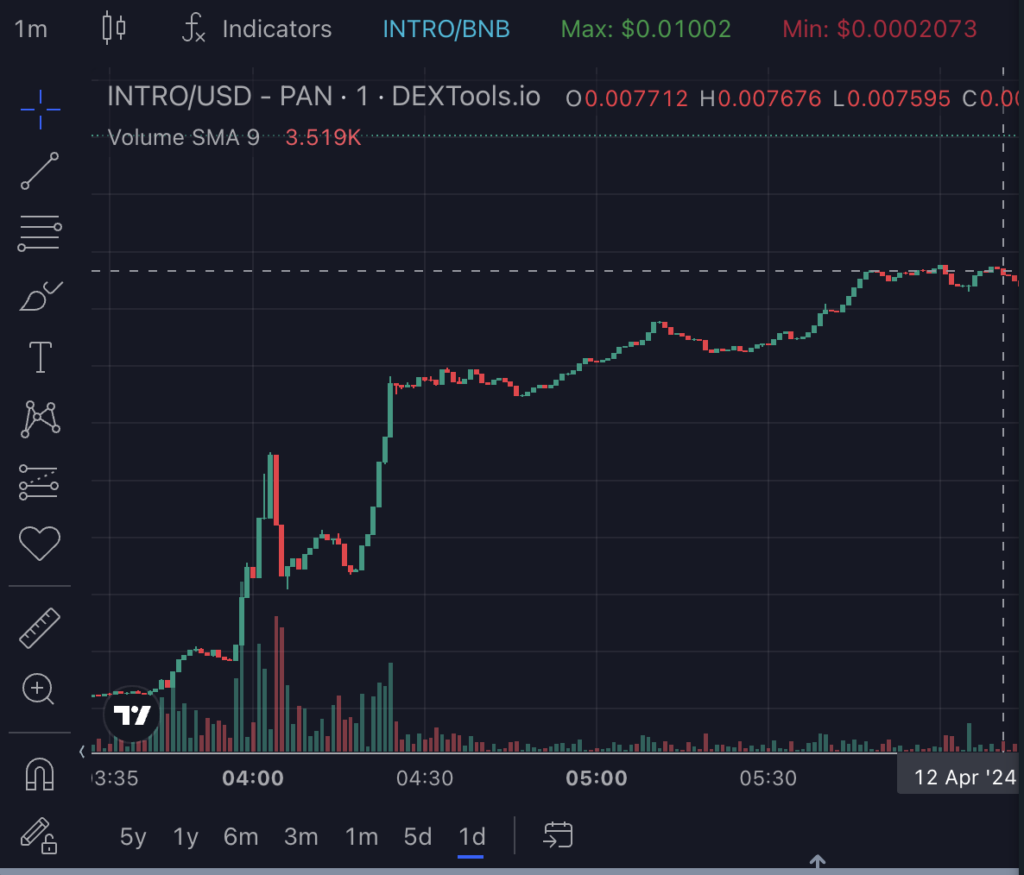
The malicious intent behind these actions becomes evident when examining the token’s design, which is structured to benefit only the owners and certain pre-designated addresses, leaving others at a high risk of losing their investments.
Deploying Rug Pull Token
The same bad actors that deploy the “SAGA” token April 10 created contracts April 12, perpetrating the same strategy for “INTRO” token.
We will examine the SAGA token rug pull to showcase how these strategies and tactics repeat:
Malicious actors deploy token0x6e21769a748fd3b819aabc8899c22dcff59eff6d using a dedicated address 0x012a8a880380b488c3a00561bdc5727eFFdEad0B, which is funded directly by a principal address 0x26ea753bb840f691c87656a01e85eca1854b7a6c. Typically, within the same transaction, a pool on a decentralized exchange (DEX) like Pancake Swap (a fork of Uniswap), is also created.
Example: https://bscscan.com/tx/0x3677780cd444e57ec5ee2ba3459d83f0c74ff2889e360c4f7c118d3d0f526c5a
Attempting to Avoid Pattern Matching
The subsequent transactions are aimed at configuring the contract, with the names of the functions being altered randomly. This tactic is employed to circumvent typical security measures that rely on pattern matching.
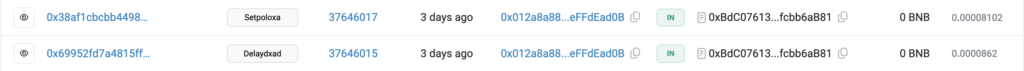
The next three transactions are designed to assign administrative privileges within the contract. The first address to be granted such privileges is 0x26ea753bb840f691c87656a01e85eca1854b7a6c, which, as previously mentioned, serves as the primary address. Additionally, administrative roles are assigned to two other addresses: 0xd018267BE360729bB5491383D24E164be4268EB0 and 0x6FC6D6926e775190cF9DBB3ad03Aa614fBa09CE8.
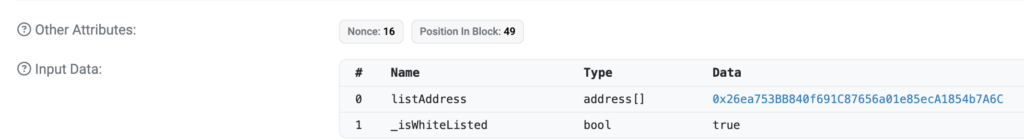
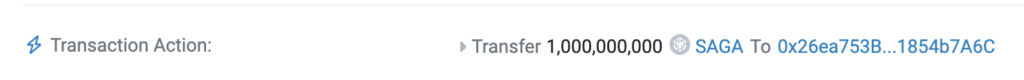
Following these configurations, the contract owner mints a significant quantity of tokens directly to the main address. https://bscscan.com/tx/0x9c5255a87d8248263fd9808bb5d3fd5aeaebb04e3081505802ae12a99dee1747
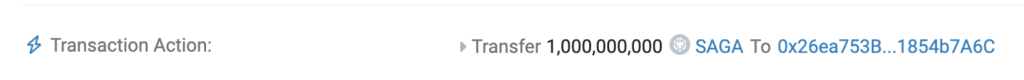
Fake Token Distribution
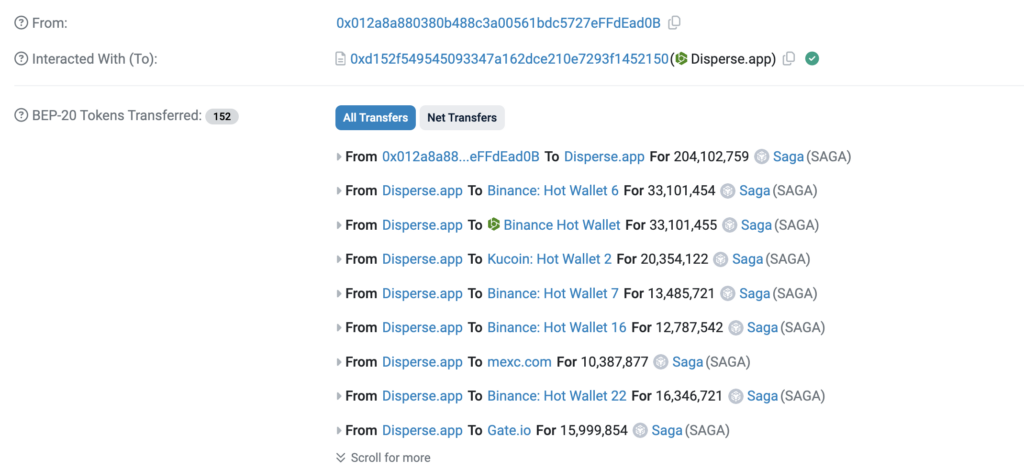
As a final step before trading begins, the malicious actor distributes a portion of the tokens, specifically 204,102,759 tokens, using Disperse.app.
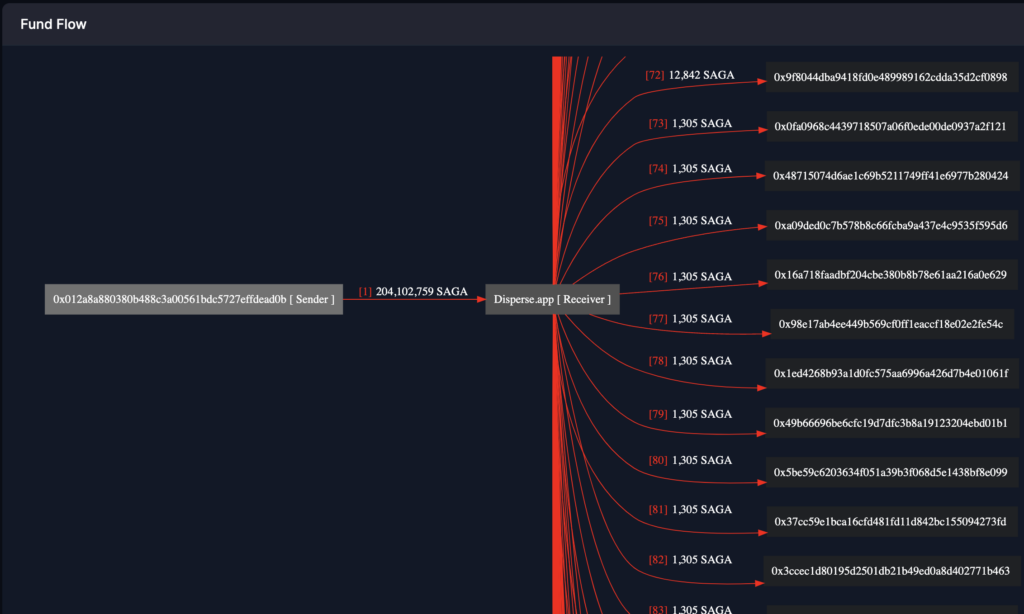
The primary objective is to allocate tokens to select, ostensibly trustworthy addresses. By employing this strategy, the malicious actor manufactures an illusion of legitimacy around the token. This perception is reinforced by the token’s association with reputable addresses and an expanded list of token holders, which many consider an indicator of trustworthiness.
Notably, the initial 12 addresses to receive the token are recognized entities within the cryptocurrency industry, including major providers such as Binance, KuCoin, and Gate.io:
The first 12 address for token distribution:
0x8894E0a0c962CB723c1976a4421c95949bE2D4E3 0xB38e8c17e38363aF6EbdCb3dAE12e0243582891D 0x53f78A071d04224B8e254E243fFfc6D9f2f3Fa23 0xe2fc31F816A9b94326492132018C3aEcC4a93aE1 0xa180Fe01B906A1bE37BE6c534a3300785b20d947 0x4982085C9e2F89F2eCb8131Eca71aFAD896e89CB 0x5a52E96BAcdaBb82fd05763E25335261B270Efcb 0x0D0707963952f2fBA59dD06f2b425ace40b492Fe 0x2e8F79aD740de90dC5F5A9F0D8D9661a60725e64 0xEB2d2F1b8c558a40207669291Fda468E50c8A0bB 0x2e8F79aD740de90dC5F5A9F0D8D9661a60725e64 0xF977814e90dA44bFA03b6295A0616a897441aceC
The remainder appears to be hardcoded addresses, which hold many tokens similar to this one. All tokens are distributed to these addresses using Disperse.app. All addresses involved can be found at the bottom of this post.*
Before starting the malicious activities, the owner completes a final step by issuing two approvals: the first enables the pool to transfer the tokens, and the second is directed to the address 0xaf71E76E8942F52Eab3D439178A5f755eb008fbc.
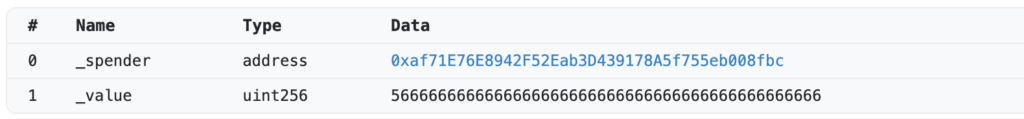
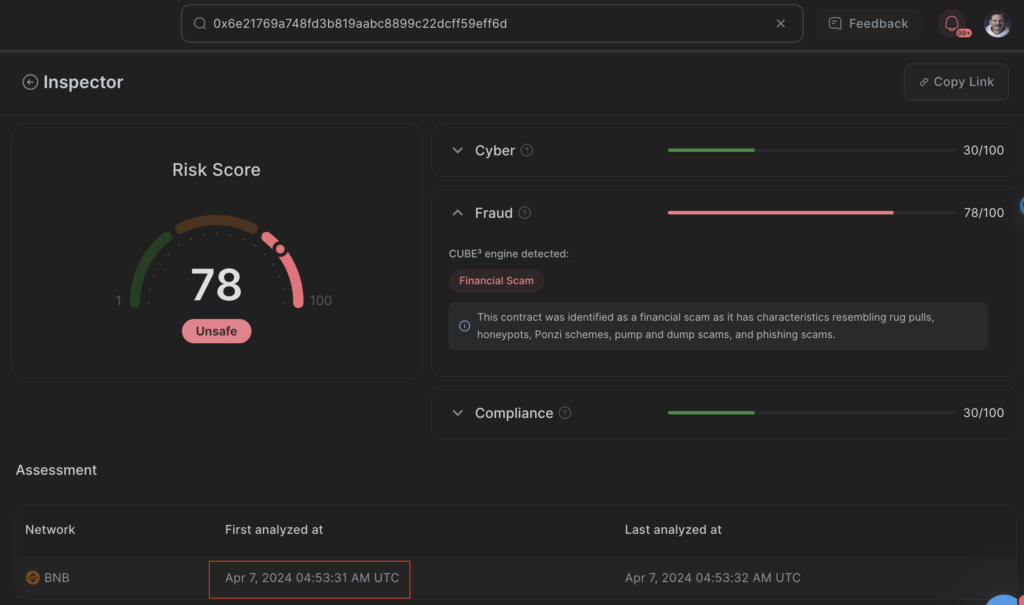
So, let’s continue with this address: 0xaf71E76E8942F52Eab3D439178A5f755eb008fbc .
CUBE3 Rug Pull Detection
CUBE detected these tokens on deployment time.
https://bscscan.com/tx/0xf5df47a83558bf8e7680435e7fcd5f752100777f0276fcf445cc5072a0df6ecf
How Are False Vibes Generated Around the Token?
Having deployed and configured their token, the malicious actors then face the challenge of attracting victims. The most effective strategy to achieve this is by creating a buzz to foster a Fear Of Missing Out (FOMO) among potential investors, who are lured by the prospect of making quick profits from new tokens. To generate this excitement and simulate a high level of activity around the token, these actors utilize transactions. In this scenario, the contract 0xaf71E76E8942F52Eab3D439178A5f755eb008fbc plays a pivotal role in assisting them.
Investors often rely on various platforms to gather information about tokens and gain insights into the projects behind them, making decisions based on factors such as:
- Whether the contract’s source code has been verified
- The count of token holders
- The distribution of holders
- The liquidity of the token
By manipulating these aspects through the aforementioned contract, malicious actors can obscure the true origins of trades. This is particularly effective on platforms where the trade initiator is identified by the ‘from’ address in a transaction. By distributing transactions across multiple addresses, it gives the false impression of widespread interest in the token.
Fake Market Trades
The first significant trade purportedly comes from a substantial investor 0xB2d4A77Ec5edfE5F49464d85CF0e041a23786A69:
https://bscscan.com/tx/0x3496807a7fdbfe17ef4a59bca38ca63dce10649a5ad0274fc7c4e253167f6e1a
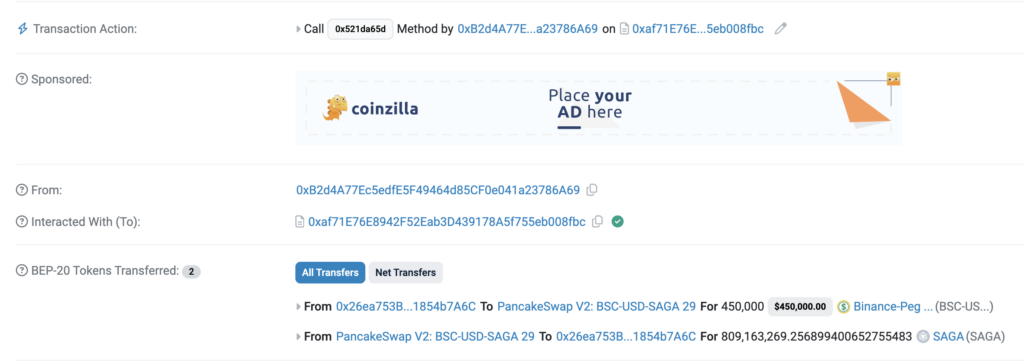
However, the reality is that the ‘main address’ (0x26ea753bb840f691c87656a01e85eca1854b7a6c) itself invests $450,000 into its own token. Subsequently, other substantial investments purportedly come from a variety of addresses, but in reality, they are all controlled by the same actor.
Given that this auxiliary contract is designed to simulate false trading activity, we can gain insight into the scheme by analyzing the number of unique addresses and transactions involved. The final tally reveals:
2,923unique addresses (EOA)- More than
99,000transactions (full list available upon request)
In this campaign, another technique also used to generate fake trade history, what you can see here:
https://bscscan.com/dex?q=0xbdc07613739a99743a86afae16c50adfcbb6ab81#transactions
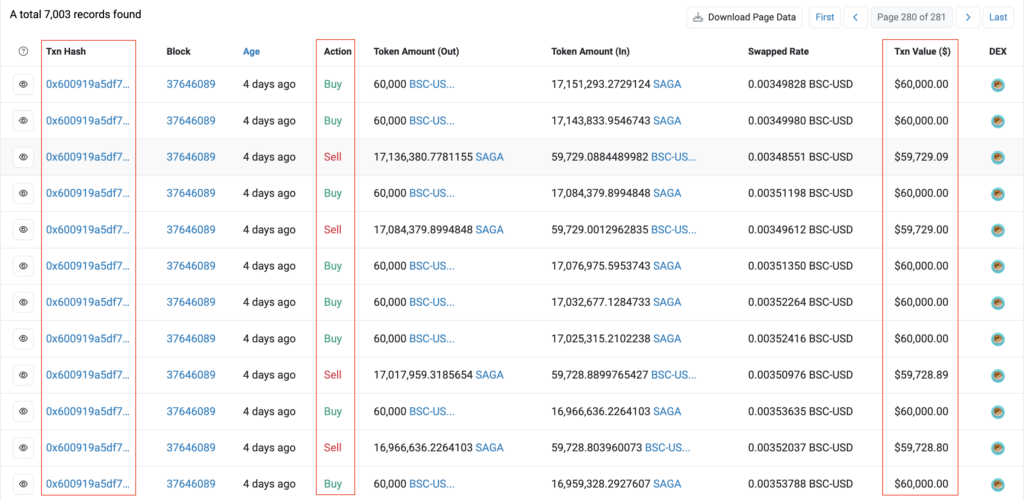
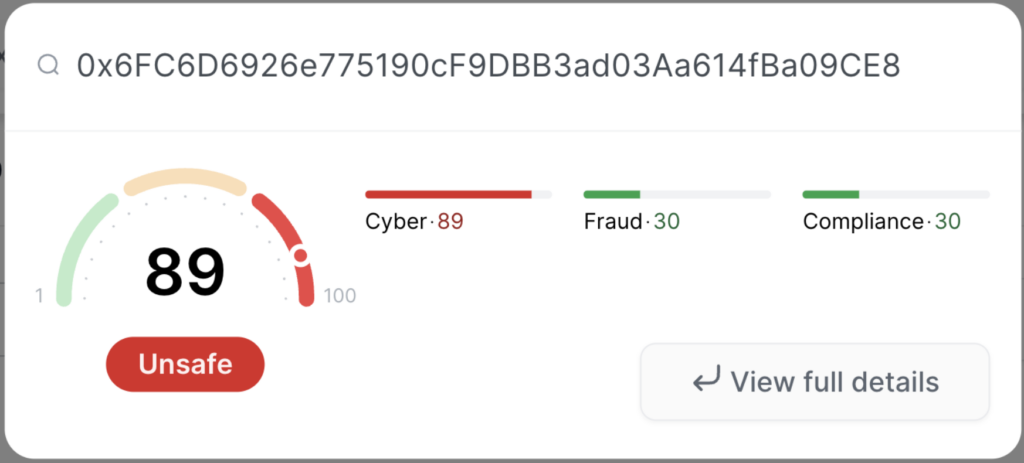
As evidenced, the token exhibits numerous buy and sell transactions. However, upon closer inspection, all trades can be traced back to a single transaction. To accomplish this, the malicious actor utilizes the contract 0x6FC6D6926e775190cF9DBB3ad03Aa614fBa09CE8, whose sole purpose is to fabricate this false trade history.
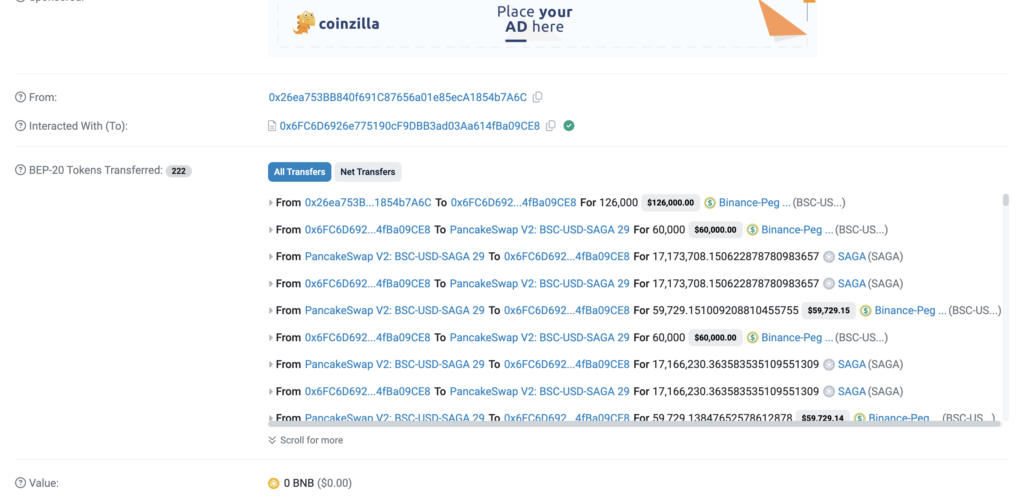
Contract address (0xaf71E76E8942F52Eab3D439178A5f755eb008fbc) tagged by CUBE3 Transaction Screening:
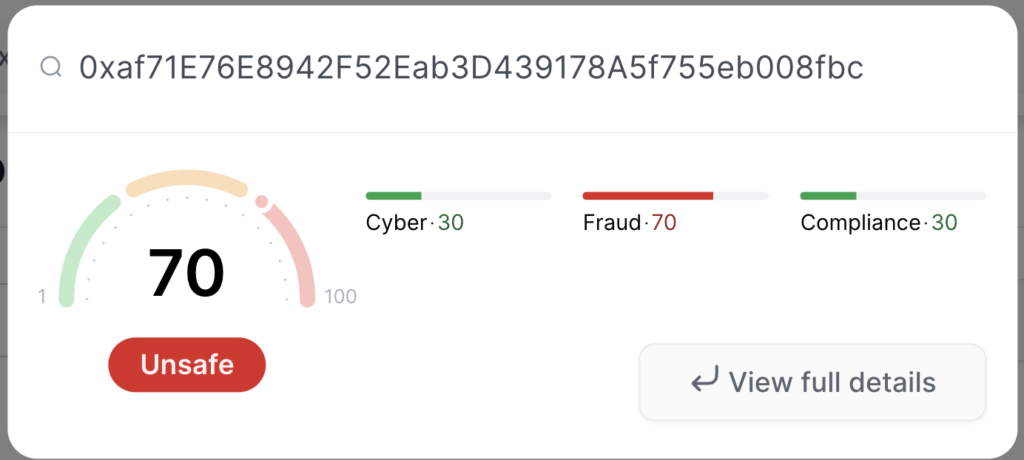
Another scam helper contract (0x6FC6D6926e775190cF9DBB3ad03Aa614fBa09CE8) was tagged by our ML as well:
Exiting the Rug Pull
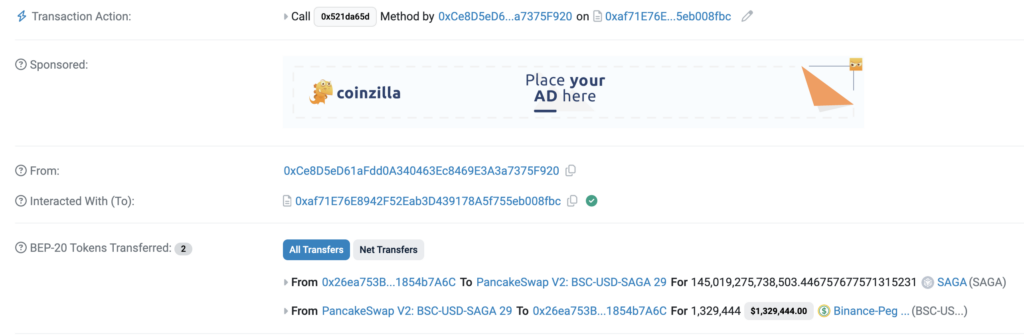
Exiting the scam is relatively straightforward for the malicious actor. Typically, they issue a ‘sell all’ command to the helper contract. As a result, liquidity is withdrawn from the pool, as demonstrated in this transaction:
https://bscscan.com/tx/0x4fefb1a36050f51efffbce9fb65d052c52851b5e1a335b8da3030d85378bf21b
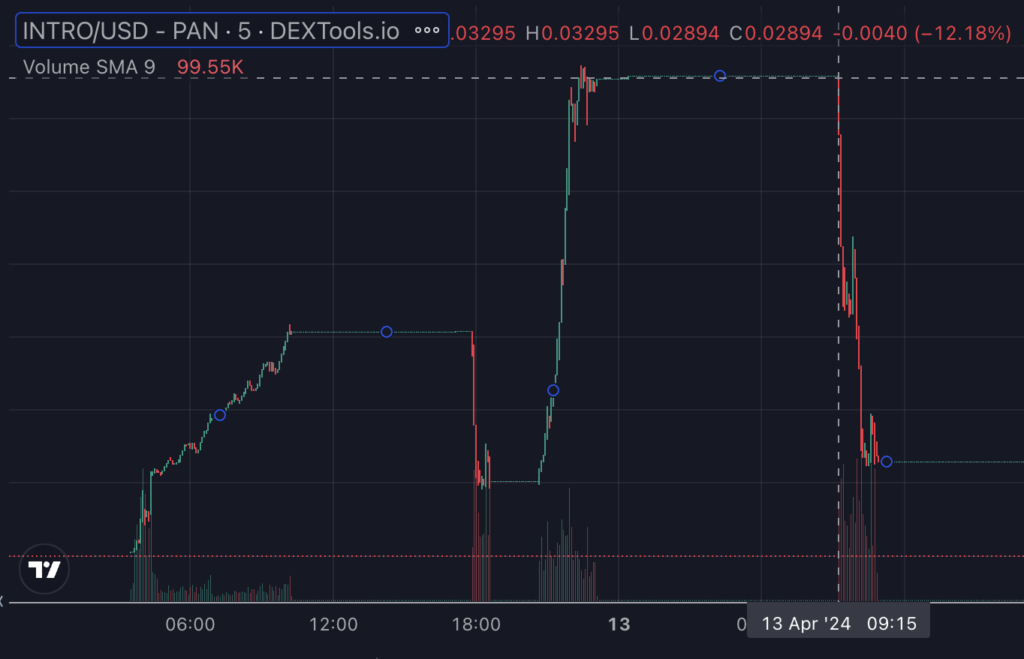
The first INTRO token rug occurred approximately 14 hours after deployment and again 30 hours after deployment:
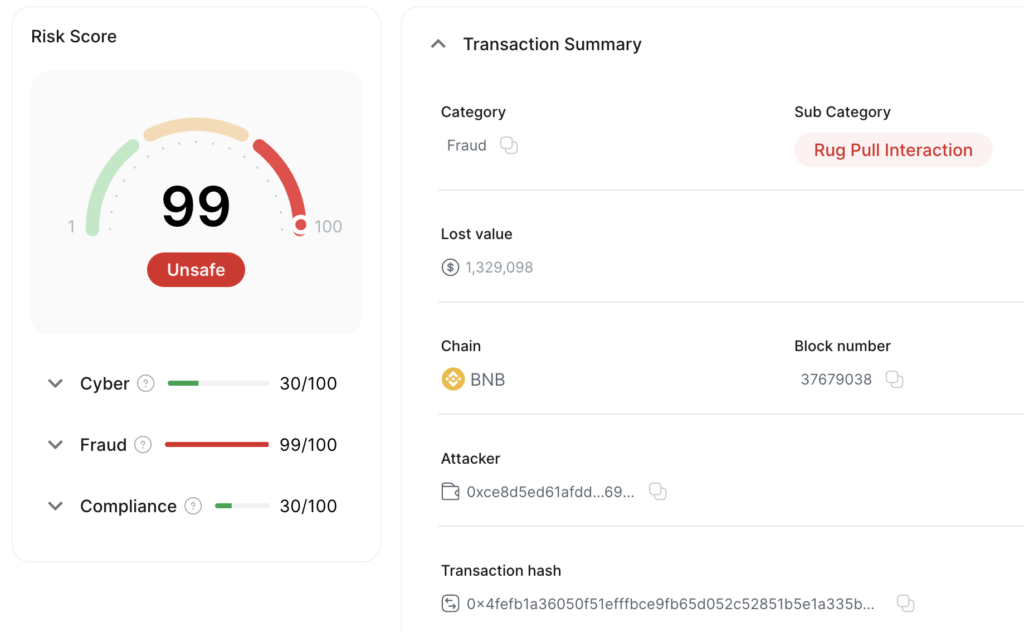
Another rug pull related to this actor here:
https://bscscan.com/tx/0x48be4020f0e19614df205b981d88dcfa9c45718abcbc4864e3ac66dd86baec90
CUBE3.AI Immediately Detects Rug Pull Transactions
CUBE3 is able to detect transaction and these types of rug pull events immediately. However, the goal for the current analysis is to ensure this type of interaction does not occur.
Why Preemptive Rug Pull Detection Matters
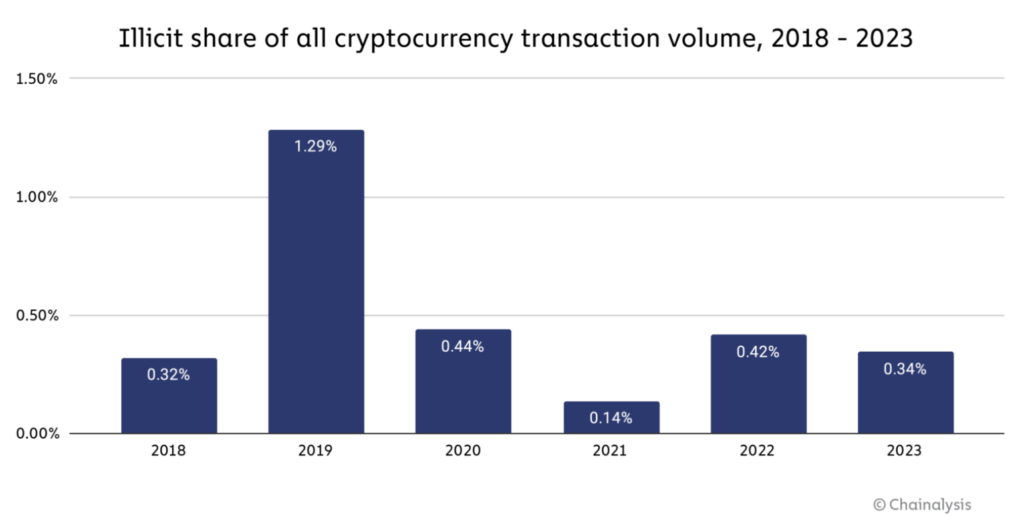
Since 2018, crypto rug pulls and scams have accounted for close to $100 billion stolen (at current prices). The good news is thanks to advanced cybersecurity systems like CUBE3.AI, the total illicit activity fell from 0.42% in 2022 to 0.34% in 2023.
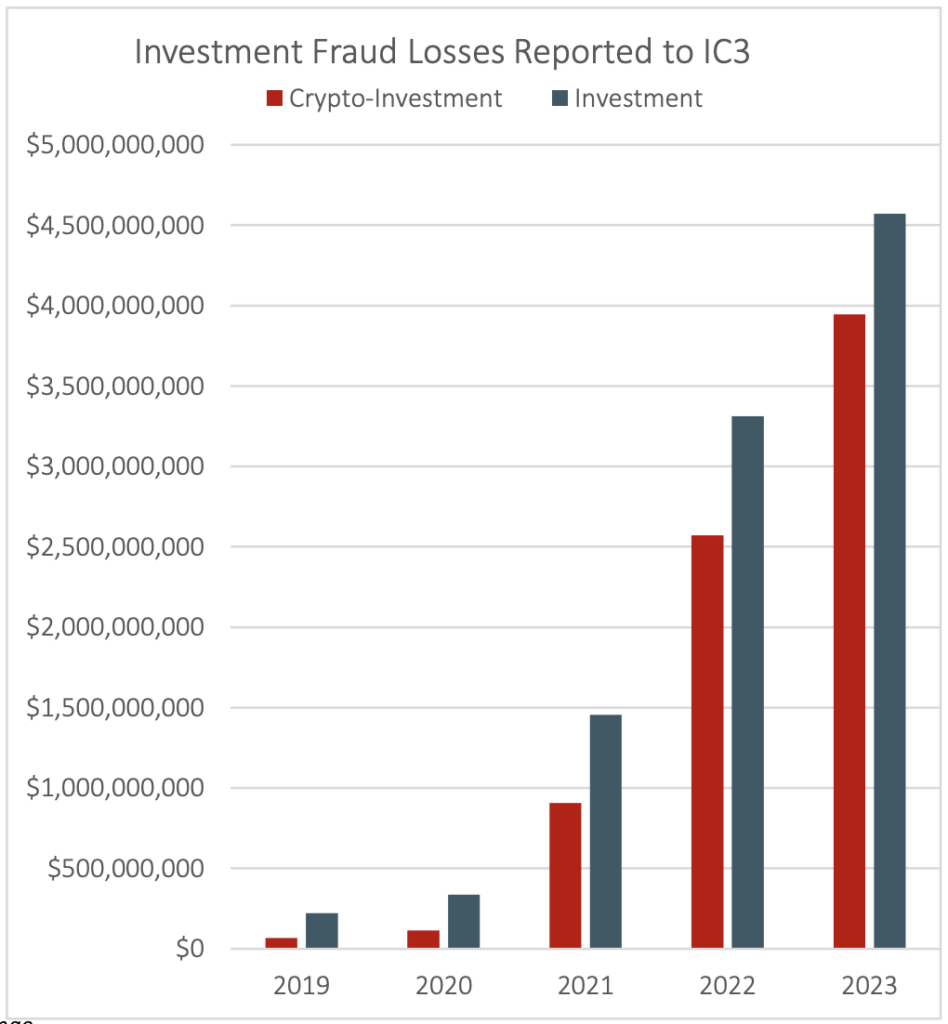
However, according to the FBI’s 2023 Internet Crime Report, investment scams are still a massive issue for DeFi, CeFi, exchanges and traders. Despite the wider downtrend of illicit cryptocurrency activity, investment scams have risen 53% from $2.57 billion in 2022 to $3.96 billion in 2023.
CUBE3.AI is here to detect, protect and manage these type of scams so the web3 ecosystem can be aware and stop these crimes from being perpetrated.
Don’t get rekt.
Don’t wait for you or your business and community to be involved in the next rug pull.
Take control of your security today. Sign up for free and integrate CUBE3’s advanced tools into your workflow.
Protect web3 with the confidence of real-time transaction protection.
*All addresses where tokens are dispersed for SAGA:
0x3826D6DfCDC26AD7213A692b911d3b3e295A8d2F
0x2922866dfe206B496F403a7432D4098C350290ed
0xacAA77CD2c12218ecDd1C8255B2E5B7865562288
0xC2949e858181B1d18f07dd1074C0b05913D1F88E
0x183c7bb2E708fae6ea8ada8f7d99c71ef4577534
0x7957b8736EC26AbeB48f5585DB166083c931bbDb
0x1535c3C680987b377BE94D090c7719835B043f59
0x91Dd7FA24B9b3438482B494B846bA1d43063F015
0x92f1e5Aa684781C38a5E9e805Df48be6EE88786e
0x5e9e23C8732379919cc98998845bcAd54abF6407
0xa5d2C497323d770322136fC5628b0D68a31C98D8
0x420A901c5504CF6587a77a4F8f63f3C88d1f704e
0xB639e24A2509c7b26438096bbd61285E745503B7
0x8603834bDc3F812B76109773A5Ea9ee68b8F8696
0x4Cc36B58148dd72D8d675800f75538F6bF9cC7Fe
0x11E52B33C8Fd0975D266625AD0f737859C10E68D
0x8930493092657e0003D543598AEF6Ec5e355176F
0x25B51E808c8678eFdACedac0f27a6a1a818Ba340
0x900B84c9474F48DB2fF267adDE90BDB12E3af5ba
0x1EC364c4568d594A32586FD3054276A91f67F49b
0xF1C7302a6D9a8F5269068ce7C8B8C40D22a9F0bF
0xA9DbC418aD593057A61Ee09bE60cf14Ff6Ca89F3
0x828dDBb74C6B0583edA187F9a010e4c2B3B5753D
0x3aAfEBCA946E92Fd12cd142511acaFc71DaB7610
0x20145df450B9DE4575122A4BA1Ee21dfE2e9cf72
0x4A69e860Aa93e01e1E130964cAEb9e12d3Df186C
0x8e64aF2267ac4Ffe0026ab4cC865F57f7F6D7dcF
0x68c7DF127E3F2410fb3ce0999aC82E18522cdF37
0xE3655ea7059B2feCf6bfeaA3748595785378410c
0xCD7D0a47e9e367e13b40B90504cE646C59cE4262
0x7335f6670C3ab3b869A1d629A97fB403522F2414
0x8c30F7d0CF91f6C940AC68d6d42eC8a8A66160B4
0xb5bEcE89da98CfEd49D52BB9665723d3979C6611
0x8fdB09aDBa54B6c1786A7CF7366Cab31057543a2
0x683dC493DD982f0b1C75db6DB04B3B82Adaf79cb
0x7fc8C473E025AF68d96B54a8663138571E214f2E
0x18dB94768DF9cBe5FeA25AF0D246E134d800b47e
0x8f63D327367479cc7feaA0aB3a808De72E2B2C2E
0x86B49A8a97183420F6c0435447F85E9ECbD2175b
0x667d1B0D5e5eaF6E4ED652b035d8218dFCD986F9
0x4B3538916E1Ca15D3646C2C70F5aC993335535A6
0x8058C74B9F1bC8045b4114Bf98f51A24012BF043
0x77408CB63BF0873080071B34E6D8B29F1AA27452
0x45c93a2b07535b681746222353BC7a5d53750957
0xEEFDd54FB60df70Ccd2E2a1Aafe4c9D252Cb6539
0x557785cD9a9B2dc0569242dE396Cd40B8E3344CD
0xA7098CEa1A866bC0139B2351A94eb7611a316041
0x18CDae8BD1C8dc4616938b6D0078272264AD9D84
0xAC4731584383413C1D6B03B784Dd395824358940
0x9Ff3bB2e9984aeEeA1AeE3723e950DEDDF605fBD
0xC710Af31b465a3223de5FD861A22C1Cf4D61f95B
0x5087D7d00248861948cdE6B2bF0c40e66959d2f9
0x59FBFEa444fD3dC3fBC1A75198fD4f54b3045933
0xAc4584f5622660114C20BFAefe566596d2E644ef
0x5AeA3dBA3a296F4639E27aBaef4814E2f3A51Ba5
0x9F19B8754c7D11A1ddF6AD334e7CA50fD98cFAf9
0xCeCdAA0E8Ef2713f439a949adE85E97B3277Ad76
0x54de7F0257F6776A7a48FD1607D2106555B648C5
0x156d3aB9a2E89F4f574a9C1105Af4BA23D26E2C5
0x9f8044dba9418FD0E489989162cDdA35d2Cf0898
0x0FA0968c4439718507a06f0EDE00DE0937a2f121
0x48715074d6ae1C69B5211749FF41e6977B280424
0xA09DED0C7B578b8c66fCba9A437e4C9535F595d6
0x16a718faAdBf204CBe380b8B78E61aa216a0E629
0x98E17ab4Ee449B569CF0FF1eaCcf18E02E2Fe54C
0x1ED4268b93a1D0Fc575Aa6996a426D7B4E01061f
0x49b66696bE6cfC19d7dfc3B8A19123204EBD01B1
0x5BE59c6203634F051a39B3f068d5E1438BF8e099
0x37cC59e1bCA16cfd481fd11D842Bc155094273FD
0x3cCec1d80195d2501Db21B49Ed0a8D402771b463
0xEC1fB6C8e2Cdae99f4EE224B5b5E6e5982560241
0x0d8e9Da39c6B576E5778Ea5FC7537dF1B6F0B217
0x56E5864E950E080100AdDD622942Fa5cB0028485
0x2E5E234b3e07C867480f66B339Ad42D3103998e7
0xedC39b34eB37DCeDbe48dd4452ca04A5285E06E8
0x5EEc63953C588B9B18b11a023Ffe10F98Fc2ef92
0x03886CdbAC80c3e17be955E8d8b3A8eEd3BCEf12
0xe69d8b7fd00dbC2a4Eb53DECa2253C9e993A1F21
0x1483523740d5597897D7b797d1CDc609f5c49b09
0xcAfF91D3AF4CC036E5eBDb60Eb3409Ec2616b8a0
0x7D4C77D552a387c9d43163E9C2F19e65891FfA5C
0xEC6d9EE2eBf6Af0A81073bB3462748cc27B25BaE
0x795c34c01bb7dFcdF1d12B55C59c02361e610c5A
0x97568551Ac35DDB7a5504B827854BD592E5F8142
0x03F565F75D382d83e26efD89C56681D90bC4310c
0xF5c8332Df68bb13d49A47F564147027235950918
0x3909378D32081Cc8fF49313C5A1BA0a7202a5Fc5
0x507C1fD8048910b4F8212a93377116691dCFAF4a
0x9EEAC2686bD9dA93274E0540F8f5308BC1fBC9C4
0x8E51cc3B3C4784Ff6B6CF41f24d4303B9b9683A0
0xe96D3Bd479139E4D0935a084cf8B4B8cf00A7C70
0x8A77d49d22e08186fC1e669035c10B6189859384
0x71269912E48a96bdf77801238f097aFA6D753FEA
0x6b9f7AeA349B34Ee549B4E2d41FcC51114A22449
0x7914a07297d63522F064f0ccf4e6487aD62C3a7B
0xb433470B09b9c558125560d9AA66abDF4fee2044
0xab02f7b8A8Bf5eB32EBEB3A53BB8282e7C4FC2c7
0x63f46dD92D33140C2798A2f82219fC2ef67adba8
0x0944AEfD213a38544a68cB01258B390cEF7677C4
0x150E1DF6f0aE72F98a6B9E82A2bfB1Ce05a36843
0x0dfFBb93Adf1F255e5Ffd7291481412dbEd287F0
0x3Ca9D54eE02d8a2Af4D4Bc055E38A5B7dfB9d529
0xE738f4e1D4e7aBE93Fca4bC982eb49EC93570b85
0xf6A2e7155fd4759113257F8F0D419EC32ADDA46e
0xaB7A2031Cee31FF1D3a8CcCAA2C77bFC439dA94F
0x9b1650349E051d38042375AA6456728C6cb56A7F
0xA90416D40a40eDFF135fa9015afe217A3F21AB70
0x9904d36a42980e75424aa28852FCA4f9c55814b0
0x2eEa117B28c42AA759cf32343B55F582D9cb4375
0x67Da6Ca5E446FE9780850b312f9C06C3e87A76f4
0xe61F4d5953634143945254f6Bb0c018C03b1766e
0x4Fe9c06280640513734de643cb9C672fFDf3aBC3
0x93f72e37CAA6324832e19a35317565dE06a79053
0x751E72F2ebe1173186ff3bEa37C1E2298B58191D
0xea3Edb80B48A1B91edED2F3D5DFA94e5d0799E7d
0xBa83c0E13b532A79999C12525CD33a494fF8D87c
0x5E7899c21237F2Cd8a07a49ae798301598c59217
0x5226f514E13B418c009e188c4BfC682F943C0044
0x8073af7516dAD42760e5F06F5a829b4a31642175
0x2a1365F08b52153fa48013fd5404b34E9cf808bA
0x7C8Cd42EFe680d94c04d4DaA134A14a0629e0844
0xE68D0162994a536aFC650B8B98749537DF45B929
0x3EdDc9c31B9d7972d0B02fE7b9952EC04b0f329b
0x7174d77dfe36C81Df786114AB17593De9F619482
0xEfD420353F02f44afFcF50e405857EEBE1eE75De
0xC4c7A9a197A5636BB58e47953DF8c05B27c6F5eB
0x71669a2eF0C6cC15D15234845493a71D05E59241
0x241A577c5966452D2Ae659e29ED3FBaBFc7D4606
0xF450B98991521Eb02c0B20Ca82efFf49D4D03739
0xB88E0B23ebB651a25fC0f8d5Ee7d500BD5167Fc1
0xF3D9Bb9ee8984E7946d804c01726007b14cE86c5
0x299b22F1134D03247d038b243DCdC53A78271f32
0x57B516619d69573659253aD2CfF7e3202BF46771
0x1d10EE991DD460137B979eb2831beC5912598fE6
0x8Bf659493155BfDA350F7A41C64561a9EA3462ae
0xD400e2C74367c06bdF9bA9582C899FF44955eCF8
0x6B2CcdbeDf0FD6f6108d781f36837f469ca813AA
0xc179e5042FCaf4F26b789b94F023E8Cc1472afDb
0xbf3f21ab728AE1EC1fA3a5140f49791AB1003aCF
 Tamás Kelemen
Tamás Kelemen

 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius


 Einaras Gravrock
Einaras Gravrock






















