
Content
Social Engineering Scams: How Fraudsters Trick Employees—and How to Stop Them
A lot of fraud targeting businesses actually starts with… people.
A text from the “CEO” asking for urgent action.
An email from a vendor with a slightly altered domain.
A customer support request from someone impersonating a high-value client.
Technology is critical in stopping fraud, but human decisions still create vulnerabilities. Fraudsters don’t break in—they often get invited in by manipulating employees through social engineering. While real-time fraud prevention tools can detect and stop fraudulent transactions, businesses also need well-trained teams that recognize fraud before it succeeds.
Here’s how to train your team to spot social engineering, identify red flags, and avoid costly mistakes before they happen.
1. Social Engineering is the Easiest Way In—And It’s Getting Harder to Spot
Fraudsters don’t just send random phishing emails—they study their targets, impersonate real people, and create convincing scenarios to make scams look like normal business requests.
How Scammers Trick Employees into Authorizing Fraudulent Transactions
Fake executive and vendor requests
Scammers impersonate a CEO, finance lead, or a trusted vendor to request urgent payments or account changes.
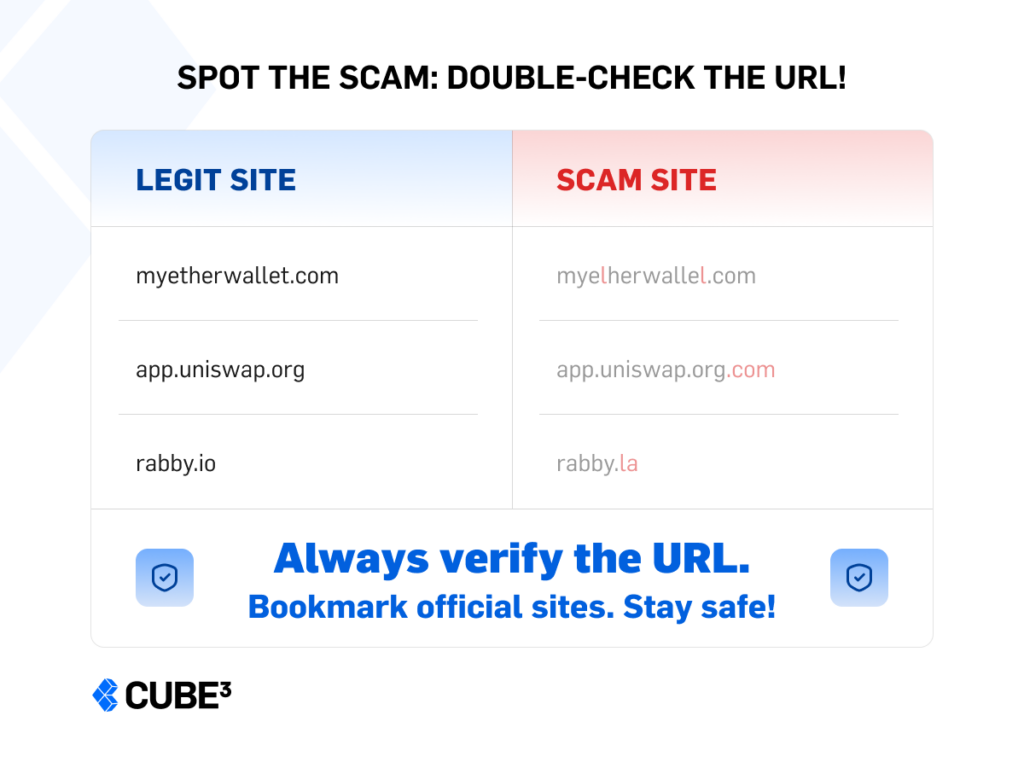
- They use fake domains with tiny changes like replacing “i” with “l” in a domain name or adding a hyphen (e.g., payrnents.com instead of payments.com).
- They send fraudulent invoices, knowing that finance teams process hundreds of transactions daily and may not question a familiar-looking request.
Compromised accounts used internally
If an employee or vendor account is hacked, fraudsters send requests from a legitimate email, making the scam far more convincing.
- They may request password resets or change payout details, rerouting funds to their wallets.
Malicious attachments and fake login pages
Employees receive an email with a PDF attachment or a link asking them to log in to “update payment details.”
- The link leads to a fake login page designed to steal credentials.
- Once inside, fraudsters initiate unauthorized withdrawals or approvals.
AI-generated deepfakes and voice cloning
Attackers use AI-generated audio and video to impersonate executives or partners, making fake requests seem real.
A deepfake call from a “CEO” asking finance to process a payment is no longer science fiction—it’s already happening.
How to Train Employees to Spot It
Verify requests through a second channel
No financial transaction, account change, or password reset should be approved based on email or chat alone. Always confirm using a trusted method like calling a known phone number listed in official records.
Check for small but critical red flags
Train employees to inspect email domains, attachments, and message tone for inconsistencies.
Make ‘pausing before action’ standard practice
Fraud works when employees feel rushed. Slowing down stops mistakes.
2. Real-World Simulations – The Best Fraud Training is Experience
Most employees think they’d recognize a scam—but would they?
Fraud awareness training only works if employees experience real fraud scenarios. Running phishing and social engineering simulations tests their ability to spot fraud before it happens.
How to Run Effective Simulations
Send fake phishing emails
Mimic real fraud attempts, including fake invoices, account verification requests, and urgent payment approvals.
Test messaging and phone scams
Call employees pretending to be IT, finance, or customer support, requesting password resets or security approvals.
Track who falls for it and provide instant feedback
Employees who fail the test should receive real-time coaching on what to look for next time.
3. Fraud Works Because People Feel Rushed—Fix That
Most fraud happens because employees feel pressure to act fast. Scammers rely on urgency, authority, and secrecy.
“I’m traveling—please send this payment immediately.”
“Your account is at risk! Click here to verify before it’s locked.”
“Our compliance team needs a security check—please reset your password.”
How to Stop This
Require multi-person approval for high-impact actions
Payments, account resets, and security changes should always require a second approval.
Use a ‘pause and verify’ rule
Employees should pause for two minutes before acting on urgent, high-risk requests.
Reinforce that security delays are good delays
No one should feel pressured to “just approve it” without verification.
4. Due Diligence and Transaction Verification – The Overlooked Step
Fraud prevention isn’t just about employees—it’s about verifying the businesses, partners, and transactions you interact with.
Verify vendor and partner reputations
Before approving payments, ensure new vendors and partners have a track record of legitimacy.
Check transaction risk before processing
Fraudsters often route funds through multiple layers of transactions to launder stolen crypto or scam proceeds.
Use risk-based screening
Real-time fraud prevention tools analyze wallet behavior, detecting whether an address is tied to fraud, scams, or illicit activity.
Many fraud attempts aren’t obvious at the transaction level—they look like standard payments until analyzed with real-time risk detection.
5. Knowledge + Technology = Strongest Fraud Prevention
No amount of training will completely eliminate fraud risks. That’s why the best protection is a combination of well-trained teams and real-time fraud prevention technology.
Technology can detect risks instantly
Identifying high-risk wallets, suspicious transactions, or abnormal behaviors before fraud happens.
Human decision-making can help prevent fraud escalation
While many fraud threats are detected automatically, trained employees who pause, verify, and report add an additional layer of protection.
Together, they create a multi-layered defense
Reducing both human error and transactional risk.
The Bottom Line: Fraud Prevention Starts with People AND Systems
Fraud doesn’t always start on the blockchain—it starts with a decision.
✔️ Social engineering attacks are getting more sophisticated – AI-powered impersonation and fake emails make fraud harder to spot.
✔️ Most employees think they’d recognize fraud—but don’t – Real-world training and phishing simulations are critical.
✔️ Fraud is easier to prevent than undo – Slowing down, verifying, and reporting can block it before money moves.
✔️ Technology + well-trained teams = strongest protection – Detect fraud early, intervene fast, and prevent losses before they happen.

 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius

 Tamás Kelemen
Tamás Kelemen

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Einaras Gravrock
Einaras Gravrock




















