
Founder, CEO
Exploring the Web3 Security Stack
Evolving Tools, Threats and Tactics
Here at CUBE3.AI, we’ve been having a lot of conversations with companies about web3 security tools and noticed a theme: Threat protection takes many forms and some solutions can be conflated. Audits, bug bounties, threat simulators, monitoring, and incident response are all necessary layers in cybersecurity best practices, but there is still a massive web3 security gap that has yet to be filled.
CUBE3.AI is pioneering a category of real-time transaction security that goes beyond monitoring and blocks threats before they occur. First, let’s clarify where we fit in this ecosystem, starting with a simple analogy:
Smoke alarms alert you of a fire, but they can’t prevent them.
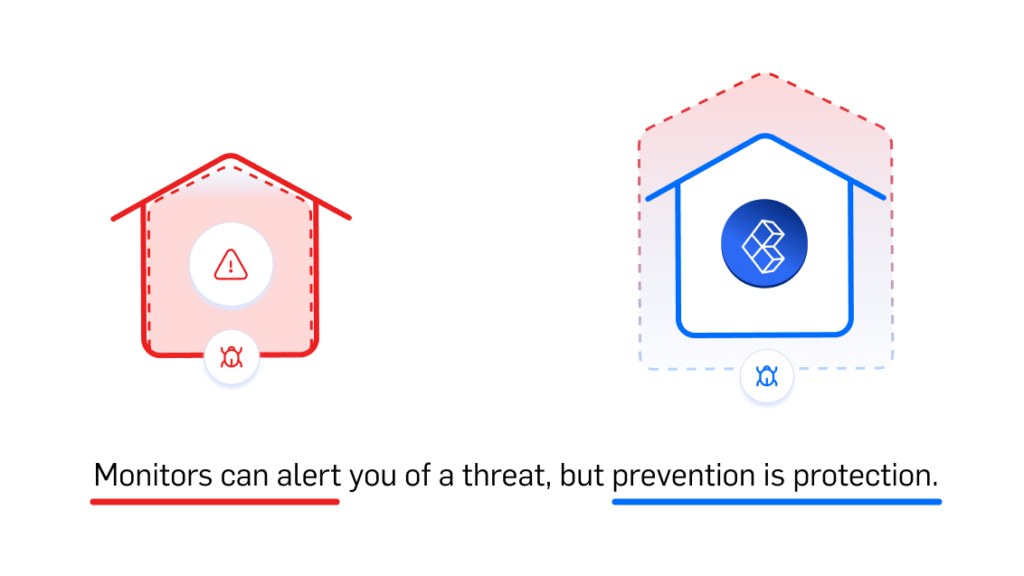
Alerts of a malicious cyberattack on your smart contract might mitigate damage, but the best protection is prevention. That’s why we created CUBE3.AI – the web3 security platform that blocks threats in real-time.
To better understand the scope of tools to protect your community and business, we’ll examine existing code security and remediation categories and provide some guidance for each to help clarify the full spectrum of solutions. Security can be broken down into two categories: pre- and post-deployment. If you’d like to learn more about each of CUBE3’s real-time transaction security products, review our DETECT, PROTECT and MANAGE product pages or reach out at [email protected] – we’re here to help.
Pre-Deployment Web3 Security Tools
Pre-deployment security focuses on tools used as part of the testing and development process, as well as external security audits.
Audits
Smart contract auditing is fundamental to any deployment process. Internally, you can use security analysis tools for EVM-compatible blockchains like Mythril, Slither or Pyrometer.
Although external audits can command a large budget, it’s important to invest upfront in order to mitigate code errors, known issues and protect from emerging threats. We recommend our partners at Least Authority and Resonance for their experience and attention to customer success. Other industry firms worth exploring:
TrailOfBits, Quantstamp, Halborn, Consensys Diligence, FYEO.
Some companies appreciate one auditor on retainer. This strategy provides firm continuity with deep protocol awareness and familiarity with your code as it evolves over time. It’s also never a bad idea to have multiple firms check your team’s work as well.
- Here is a helpful guide on how to prepare for an audit from Consensus Diligence
Bug Bounties
After you have jumped through the audit hoops and are prepared to deploy your code, it’s important to get a trusted group or community to perform Bug Bounties. Bounties are an essential part of any protocol or ecosystem that encourage responsible disclosures of vulnerabilities post-deployment. Seek support from the following platforms: Immunefi, Sherlock.
Simulators
Throughout this process, keep testing your code for security vulnerabilities through dynamic analysis penetration testing. Cross-check with a formal verification process (may be part of the audit process). Ensure your contract only executes that which is required to do. A good place to start is Manticore.
Post-Deployment Web3 Security Tools
Incident Monitoring
This involves monitoring for breaches and exploits once they occur. Companies like Forta help protect the health of your contracts. Contact us to trial our monitoring solution (watchlist and alerts) which we’ll be releasing soon! We also take your security protection a step further. Our Runtime Application Self-Protection (RASP) Protect product is designed to block threats that are outside your risk threshold before they occur.
Incident Response
This involves helping organizations respond to security incidents, such as hacks and data breaches. Training your employees and conducting regular mock drills to ensure everyone is well-trained is a crucial preparation step. Having a codified and well-documented response plan is another best practice. Part of this should be a playbook, that includes regular communication with your team and community. If you ever identify an active threat you will be in a position to contain, and eradicate the cause. Proper incident response can maintain the trust of your company and customers.
If you need 3rd party assistance, see Hackless.io.
Web3 Security Tools – Conclusion
Despite all these best practices, we’ve seen a half a decade of DeFi hacks and even known issues are still prevalent. Euler Finance, for example, was audited by six separate firms lost $195 Million this year in a flash loan reentrancy attack. Euler’s incident response and tactics are perhaps one reason it was able to recover funds. However, together, we must layer security and stop exploits before they occur.
More community members are proposing mature and advanced web3 security protocols. We must work as a community to increase innovative progress and decrease criminal success. Human and software errors are expected, so cybercriminals use similar social engineering and software exploit in both web2 and web3 (supply chain exploit, code injection, phishing, Trojan horse, etc.). Web3 protocols are even more vulnerable due to untested attack vectors, emerging tech stacks, lucrative TVL and lack of centralized oversight.
We hope this article clarifies the layered importance of evolving web3 security tools and how CUBE3 can help fill the web3 security gap. Pre-deployment measures like audits, bug bounties, and simulators are an essential start. Effective post-deployment measures like incident monitoring and response preparation are equally valuable. CUBE3’s transaction security layer is a critical real-time defensive technique that can DETECT, PROTECT and MANAGE on-chain exploits before they occur.
Sign up and join CUBE3.AI in protecting the next evolution of web3 security tools, so you don’t risk your business and community’s assets, time, effort and trust.

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Jonathan Anastasia
Jonathan Anastasia
 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius



 Tamás Kelemen
Tamás Kelemen



















