
Chief Research Officer
When Hackers Get Hacked: Unpacking the $GPU Exploit with CUBE3.AI
“Homo homini lupus” is an ancient proverb that can be translated to “Man is no better than a wolf, to another man.” The hack of $GPU reflects a similar phrase, there’s no honor among thieves…
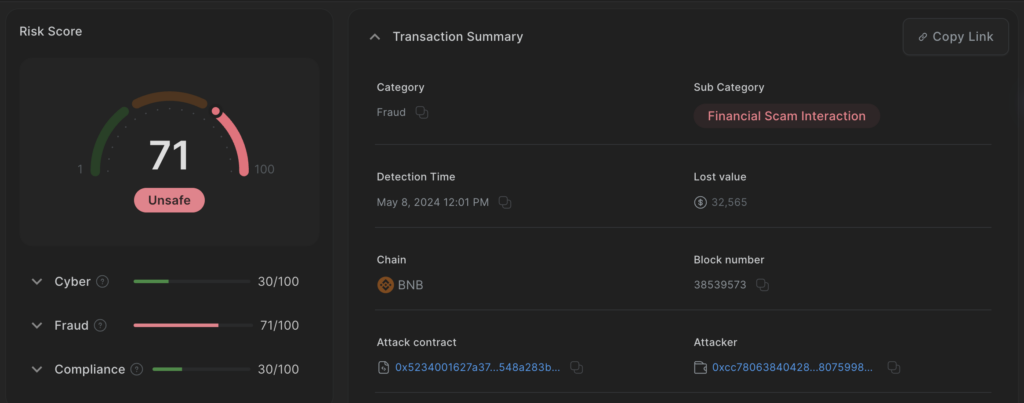
On May 8, 12:01pm (UTC), CUBE3’s AI system detected a transaction on the BNB Smart Chain with characteristics of a standard attack (0x2c0ada695a507d7a03f4f308f545c7db4847b2b2c82de79e702d655d8c95dadb):
- The contract was identified from Tornado Cash to cover tracks.
- A manipulative FlashLoan tactic was utilized.
- A significant amount of money was lost from the victim’s contract (GPU).
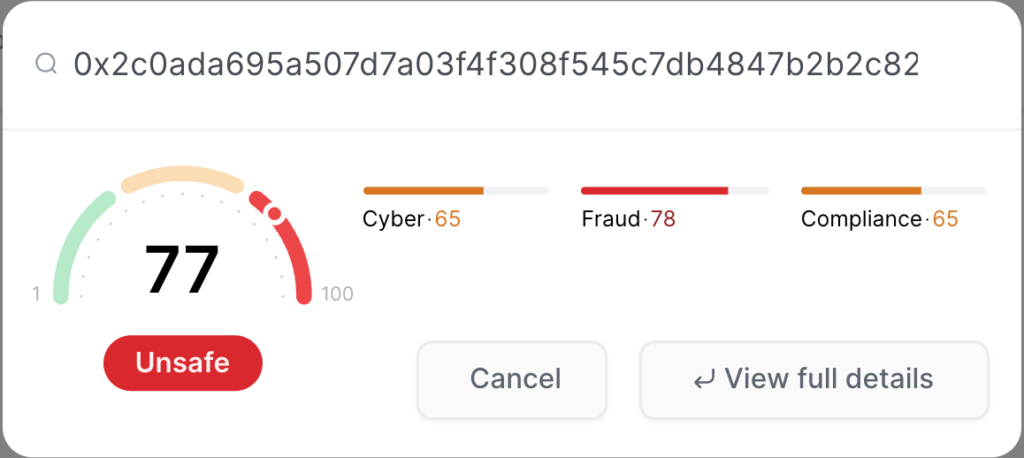
Following our detection, numerous tweets and reports surfaced about the $GPU token being hacked, with $32,000 USD reportedly stolen.
At this point, the team could have moved on but something interested me in the background of the victim. What I found was quite intriguing:
After investigating the transactions of the victim contract’s deployer, 0xd150d6f6e815656ea580ce1c6b8e0ec7f0165b47, it became apparent that this is not a typical genuine victim. This actor has been involved in financial scams for over a year. Using just this one address, the actor has deployed more than 30 contracts, all designed to steal money from others.
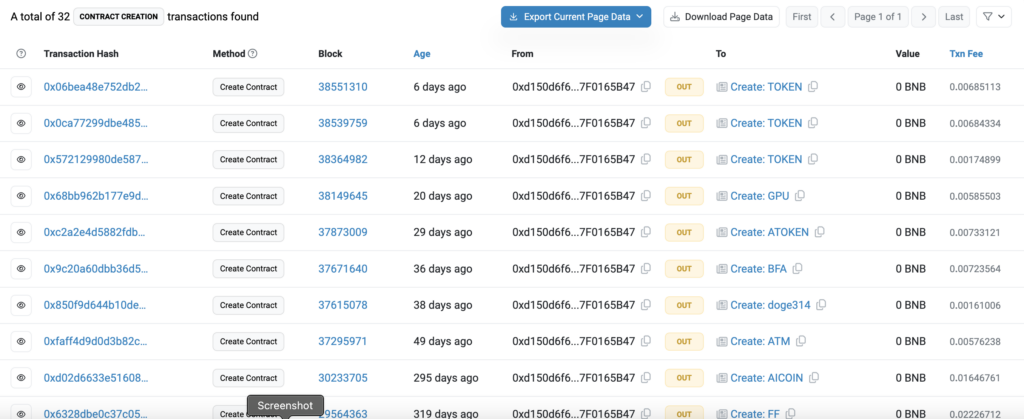
It’s also interesting to note that the vulnerability exploited a few weeks ago was first used in these contracts nearly two years ago. The first one was this: 0xf15d15f4c05697ee63ed2cc7595265446c78f8a8

The last time this actor deployed a contract with this vulnerability was nearly a year ago, 319 days to be precise. You can view the details here:
https://bscscan.com/tx/0x6328dbe0c37c05fccf08bd0612ba633725a5d9f148b421085567f30f5c00d439.
Given this timeline, we can be confident that the vulnerability was not intentionally added to the contract to provide a backdoor for the deployer. In the intervening months, other techniques were used to financially harm token investors, such as imposing a 99% fee.
However, the pattern of recent $GPU hack exploitation was markedly different. My assumption is that others have discovered this vulnerability and used it to divert money from the scammer.
The CUBE3 Research Team goes above and beyond to train our sophisticated ML models to not only detect and block threats by crypto criminals, but we dig deep into the causes of these attacks for full context. Review some of our recent postmortems from address poisoning, flashloans or rug pulls to understand more about the ways we protect your business and community.
Contact CUBE3.AI today to learn more about how our platform detects and blocks risks. In a world of evolving regulations and cyber threats, proactive risk management is key to safeguarding digital assets and ensuring the continued success of your business.
Book a call with one of our experts here: https://www.cube3.ai/book

 CUBE3.AI
CUBE3.AI



 Sarunas Matulevicius
Sarunas Matulevicius

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Einaras Gravrock
Einaras Gravrock


 Tamás Kelemen
Tamás Kelemen



















