
Chief Research Officer
CUBE3.AI Detects Multiple Price Manipulations by Same Address
CUBE3.AI detected crypto price manipulation attacks against two different tokens on Binance Smart Chain, executed by the same bad actor: 0x3026C464d3Bd6Ef0CeD0D49e80f171b58176Ce32
1. Wall Street Memes Crypto Price Manipulation Exploit ($19K)
First, the attacker address was flagged and scored because it was directly funded from Tornado Cash at 2024-04-04 16:24:07. Although not all Tornado Cash transactions are malicious, the mixer is officially listed on the US OFAC sanctions list, which consequently increases the risk score.
Seconds after the address was funded, this address deployed a contract (0x014eE3c3dE6941cb0202Dd2b30C89309e874B114) which was scored by our ML model, and categorized as an exploit contract (2024-04-04 16:24:04).
At 2024-04-04 16:25:44, one minute later, an exploit transaction occurred, which was scored by or transaction screening service as Mixer Malicious Contract.
TXN hash: 0x5a475a73343519f899527fdb9850f68f8fc73168073c72a3cff8c0c7b8a1e520
Victim Losses: $19K
Amount of token holders: 38,280 🚨
Root Cause of Wall Street Memes (WSM) Exploit
- In this transaction, the attacker used a very aggressive arbitrage trade where the price difference was generated by a flash loan.
- UniswapV3 Flash function was use on pool1 to get 5M WSM token as a flash loan.
- Subsequently, the malicious actor then sold tokens on pool2 to modify the price of the tokens and receive 37 BNB as a result.
- Victim contract
0xfb071837728455c581f370704b225ac9eabdfa4aused pool2 to get the price of WSM token ← which was just modified. - Afterward, the attacker bought 2.7M of WSM token by using the victim’s contract. Since the victim’s contract used the price of the pool2, selling tokens at a discounted price to the attacker.
- Finally, the attacker bought 4.7M WSM tokens from pool2 to have 5M to pay back the flash loan.
2. Z123 Crypto Price Manipulation Exploit ($140K)
Today, attacker activate itself again and deployed a new contract which was picked by ML service again (2024-04-22 07:55:32): 0x61Dd07Ce0cEcF0d7BaCf5EB208C57D16bBdEE168
Very soon (2024-04-22 10:02 AM), malicious transaction was detected (Mixer Malicious Contract): 0xc0c4e99a76da80a4cf43d3110364840151226c0a197c1728bb60dc3f1b3a6a27
Victim losses: $140K
Token holders count: 3,331
Root Cause of Z123 Price Manipulation
Malicious actor using Flash loan to manipulate the price of the token in pool.
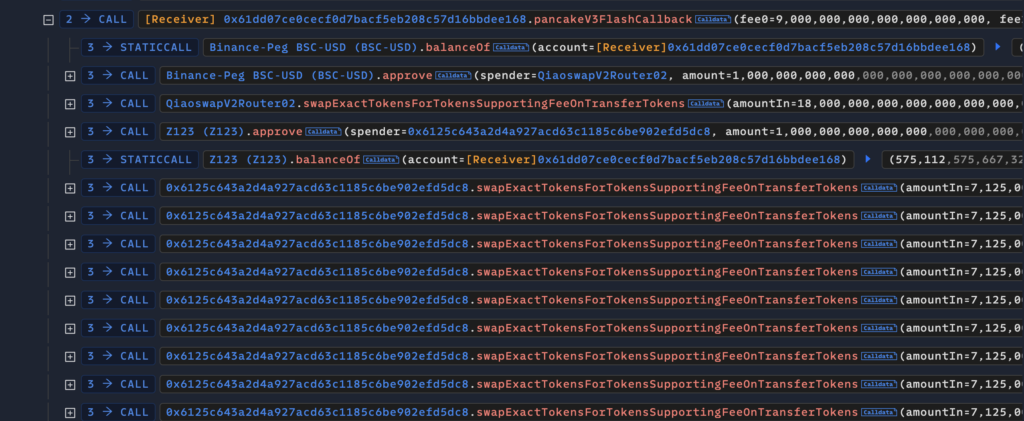
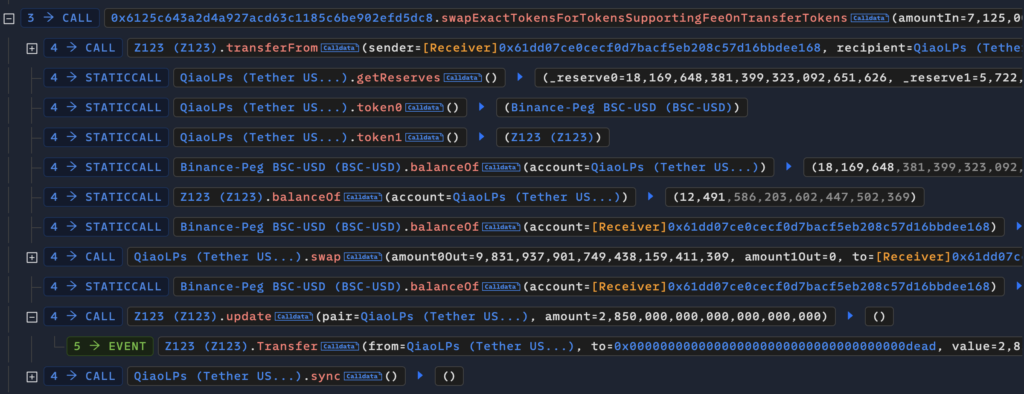
By doing 81 iterations of token swaps and calling the ‘Update’ function of the pool, the price was manipulated.
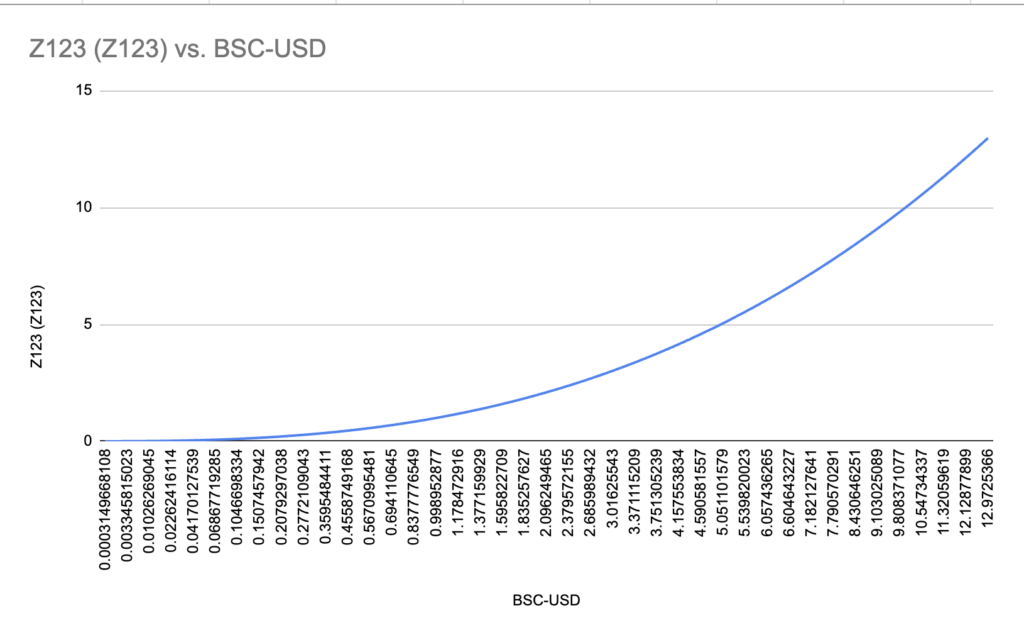
Here you can see how the price was inflated:
CUBE3 detects and blocks malicious transactions before they resolve on chain. Whether it’s crypto price manipulation, rug pulls, flashloans or one of the various compliance risks your company needs to be aware of. Take control of your security today. Sign up for free and integrate CUBE3’s advanced AI tools into your workflow.

 CUBE3.AI
CUBE3.AI
 Sarunas Matulevicius
Sarunas Matulevicius

 Silur
Silur

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Tamás Kelemen
Tamás Kelemen

 Einaras Gravrock
Einaras Gravrock




















