
Chief Research Officer
One Contract Poisoned 1 Million+ Addresses — How to Detect and Prevent Address Poisoning Scams
What is an Address Poisoning Scam?
Address poisoning is a deceptive technique where malicious actors exploit the similarities between wallet addresses to trick users.
How Does Address Poisoning Occur?
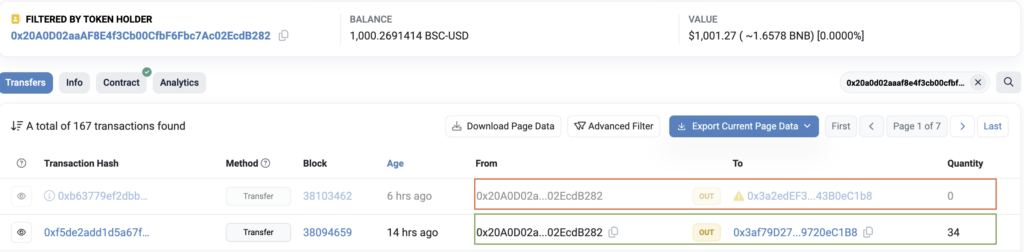
In a typical scenario, the scammer observes a legitimate transaction (highlighted in green in the image below). They then execute a fraudulent token transfer that appears almost identical to the legitimate one, but with a crucial difference; the ‘To’ address is subtly altered to resemble the victim’s usual recipient address. This fraudulent transfer typically involves a zero-value token.
What is the Outcome of an Address Poisoning?
The danger arises when the victim reviews their transaction history. Mistaking the fraudulent address for their intended recipient, they may accidentally copy this fake address for future transactions, sending valuable assets directly to the scammer. This scam primarily relies on the victim’s oversight and the complexity of blockchain addresses, which can be difficult to distinguish at a glance.
Example of An Address Poisoning Scam CUBE3.AI Detected
CUBE3.AI detected a very active malicious actor on the Binance Smart Chain, and we will describe the case in detail.
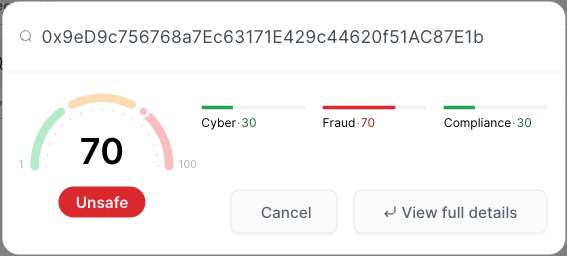
Contract address:0x9eD9c756768a7Ec63171E429c44620f51AC87E1b
As of the writing of this article, this contract is less than a week old and has astonishingly amassed 270,745 transactions. Subsequently, CUBE3 detects a high Risk Score:
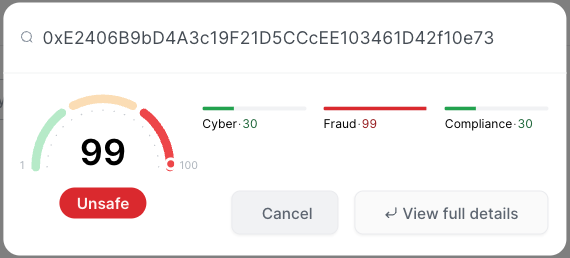
The deployer of this contract is listed as 0xE2406B9bD4A3c19F21D5CCcEE103461D42f10e73. This address is infamously linked to a series of malicious activities and a 99 CUBE3 Risk Score:
The Address Poisoning Code
As is typical with malicious contracts, the source code is not published…
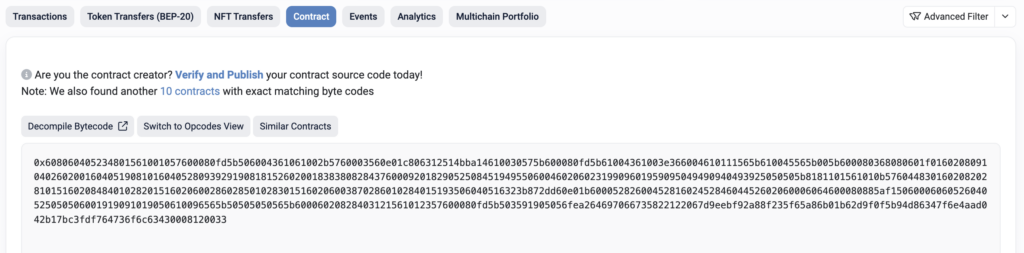
In this case, we have multiple options. If you already have a full stack of EVM decompilers implemented in your head, then you could directly read the opcode. 😄
PUSH1 0x80
PUSH1 0x40
MSTORE
CALLVALUE
DUP1
ISZERO
PUSH2 0x0010
JUMPI
PUSH1 0x00
DUP1
REVERT
JUMPDESTIf not, we need a disassembler. For this, there are multiple online services like these such as Ethereum Virtual Machine Opcodes [https://ethervm.io/]
But for this research I used a local tool called, Panoramix [https://github.com/eveem-org/panoramix].
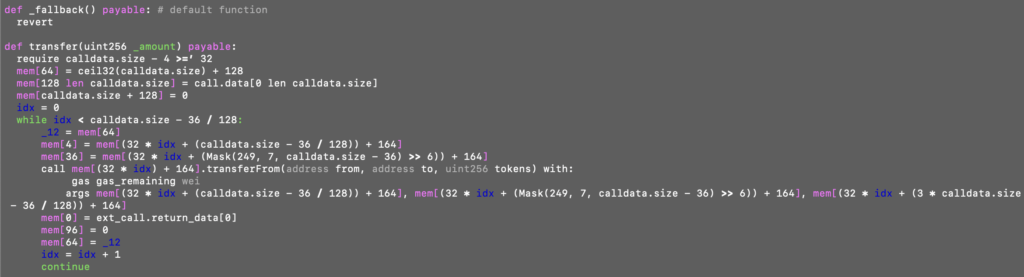
The contract is quite straightforward. It chunks calldata into pieces, with each piece specifying which address to call and what parameters to use: From, To, Amount. This contract serves as a very generic tool in the attacker’s arsenal. The actor uses this contract not only to poison addresses but also to distribute fake tokens. In these cases, fake versions of Tether, PancakeSwap, and Wrapped BNB are distributed.
How can someone send a token in my name to someone else? This is possible because the transfer value is zero and there’s no limit on the transfer of ERC20 tokens. Someone can send tokens on behalf of others as long as they have been granted an allowance to do so. The smallest allowable amount is zero; therefore, if you do not exceed this value, you can transfer tokens from person A to person B.
Ok, we know the contract, let’s see how it works with a transaction:
https://bscscan.com/tx/0x9d10ac68157c3125085e655c4d21cb3b2a3304ae1da1f62c363c2fa8330882b7
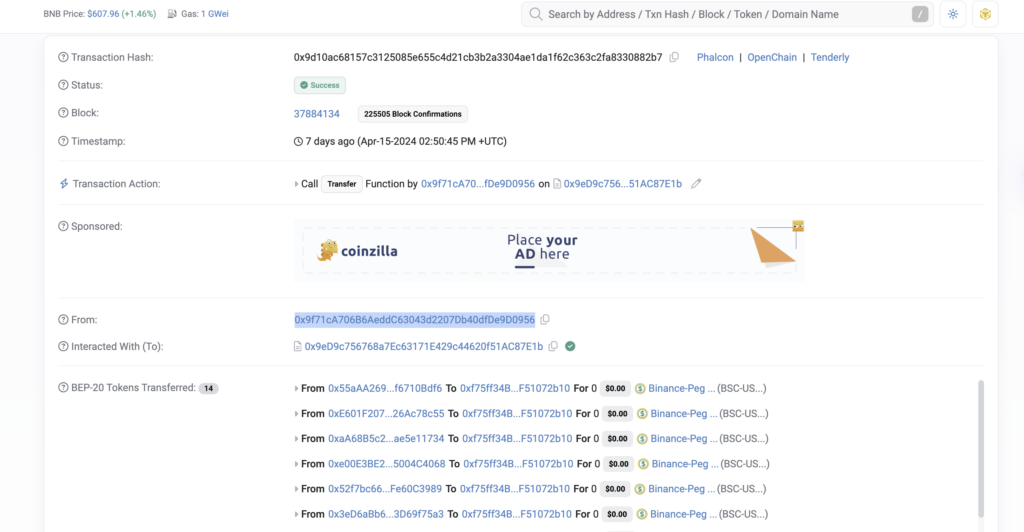
As a result of this transaction, 14 addresses were scammed with fake token transfer.
We have assessed the scope and characteristics of this case. Here are the key figures:
- ⚠️ 7,032,527 transfer events were generated by this single contract ⚠️
- Number of unique victim addresses: ⚠️ 967,090 ⚠️
- Number of unique poisoned addresses used: 1,386,231
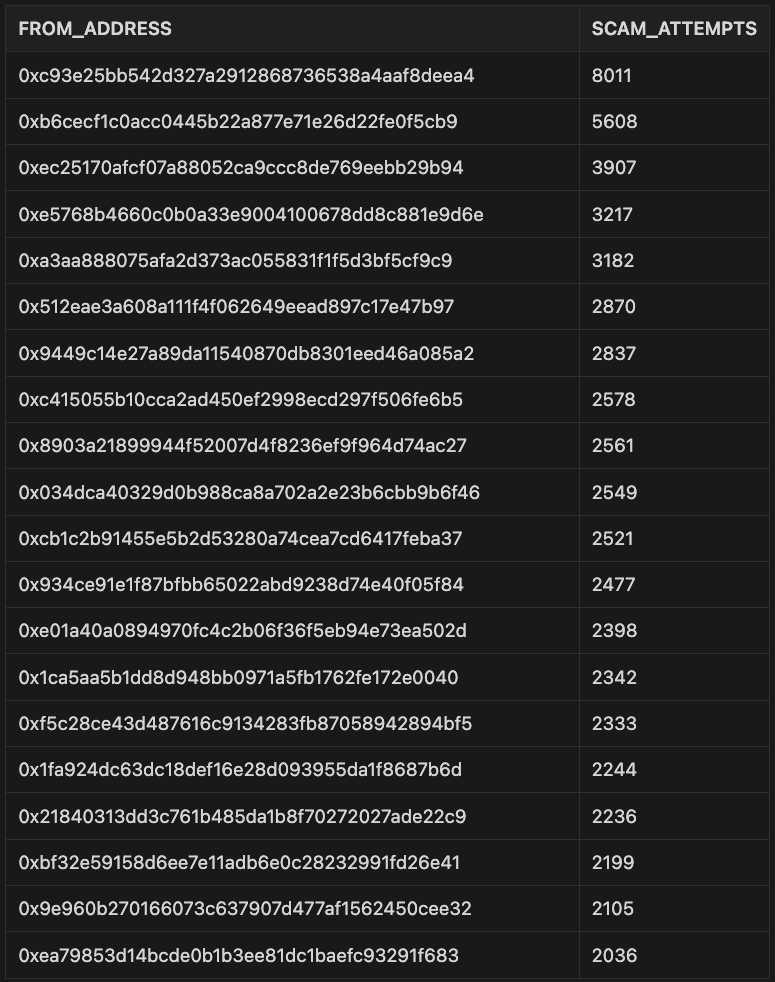
Top Scammed Addresses
We have also identified the addresses that were most frequently targeted by the scammers. Here is the top 20 list of those addresses:
How to Protect Against Address Poisoning:
- Verify addresses thoroughly: Always double-check the address you are sending tokens to, especially if you are copying it from your transaction history.
- Use address labels: Utilize wallet features that allow you to label and identify saved addresses to avoid confusion.
- Be cautious of Zero-Value Transactions: Treat unexpected zero-value transactions as potential red flags.
- Use CUBE3’s free Inspector Tool: CUBE3 Detect tools continuously monitor addresses for involvement in exploits, wallet hacks, fraud, and compliance risk. Get an address Risk Score by CUBE3 before you transact with any wallet or smart contract.
CUBE3 detects and blocks malicious transactions before they resolve on chain. Whether it’s address poisoning scams, crypto price manipulations, rug pulls, flash loans or one of the various compliance risks your company needs to be aware of.
Take control of your security today. Sign up for free and integrate CUBE3’s advanced AI tools into your workflow.

 CUBE3.AI
CUBE3.AI

 Stanislav Kutnyk
Stanislav Kutnyk
 Einaras Gravrock
Einaras Gravrock

 Sarunas Matulevicius
Sarunas Matulevicius

 Attila Marosi-Bauer
Attila Marosi-Bauer


 Tamás Kelemen
Tamás Kelemen



















