
CUBE3.AI Security Researcher
Days in Advance, CUBE3.AI Detected Sophisticated $18M UwU Lend Attack
Two days prior to the execution of the $18 million UwU Lend attack, CUBE3.AI models detected the malicious contract within seconds after deployment.
On June 10th, CUBE3.AI detected multiple malicious transactions [1] targeting UwU Lend’s LendingPool contract on Ethereum. The attack led to the theft of $18 million worth of assets through an oracle price manipulation hack. Although the protocol was previously audited, the exploit was highly complex and sophisticated. Each transaction involved nine different flash loans, four exploit helper contracts, and a contract deployment that triggered the execution.
The attackers used Tornado Cash to fund the attack [2], making it more difficult to trace the origins of the transactions.
This article will focus on the first transaction, as the other transactions were similar, differing only in minor details.
Beware of Scammers on X!
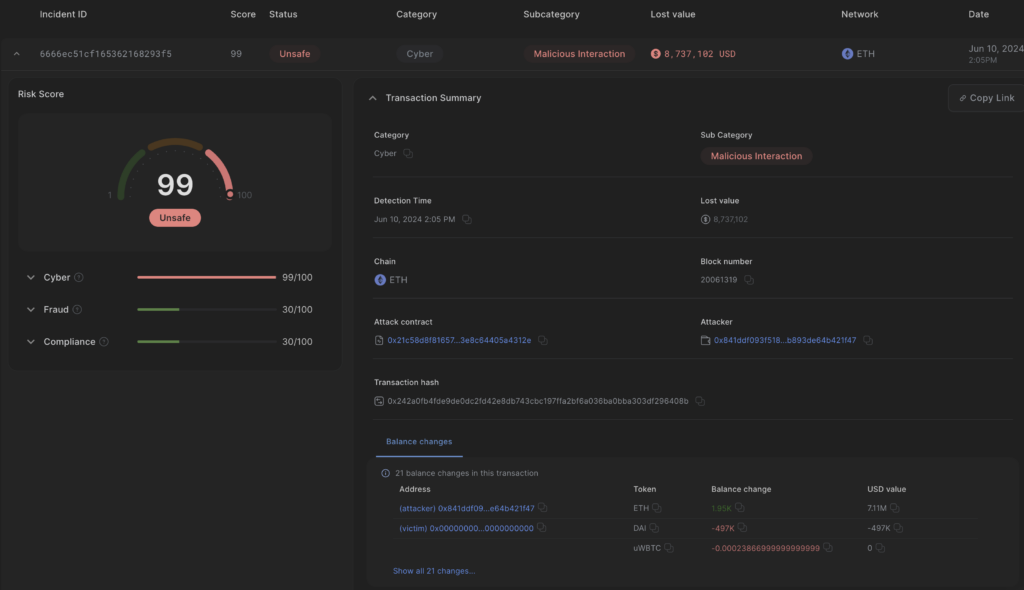
Before we dive into the details, it’s important to raise an alert of scammers that use web3 exploits to scam the web2 community. Once UwU announced the hack on Twitter, scammers began spamming the post using nearly identical Twitter handles to the official UwU account.
Notice the difference between the official UwU_Lend and the scammer’s UwU_Lendio.
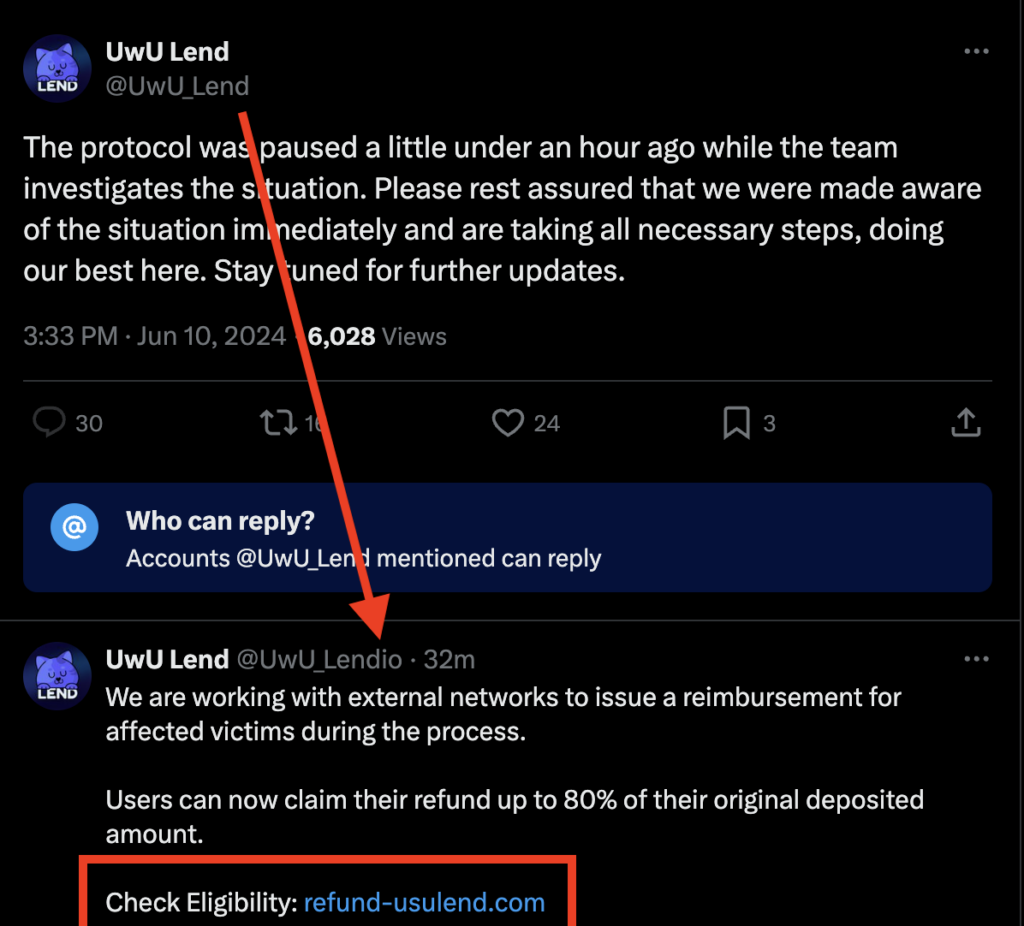
These spam comments included a malicious URL posing as a link to a “refund” site. However, clicking on this deceptive link could lead to further harm for victims, potentially losing all assets from one’s address.
It appears that the scammer used a stolen Twitter account which was created in 2012, currently with 52k followers. The fake user even went as far as retweeting multiple posts from the official UwU Twitter account. This strategy aimed to heighten the credibility of their malicious actions and make it more challenging to notice the scam.
Always verify the source of information to avoid falling victim to compounding fraud.
Participating addresses
Attacker EOA
Address: 0x841ddf093f5188989fa1524e7b893de64b421f47Funded from Tornado Cash in multiple transactions [2], each sending ~1 ETH to the address, adding up ~6 ETH total.
Exploit contracts
Exploit contract 1
Address: 0x4fea76b66db8b548842349dc01c85278da3925daDeployed at: Jun 8, 2024 06:14:11 AM UTC
Detected at: Jun 8, 2024 06:14:32 AM UTC
Used for handling and receiving flash loans from multiple providers.
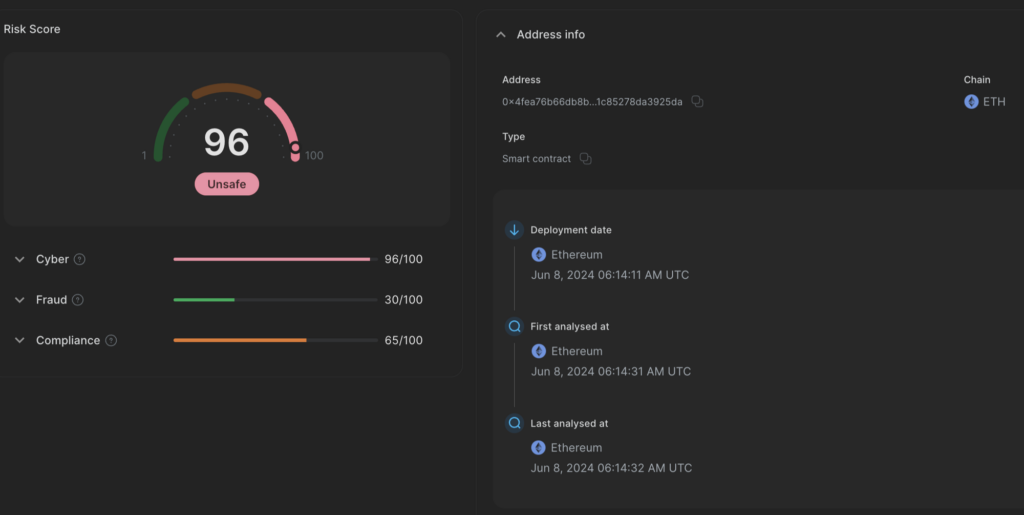
Exploit contract 2
Address: 0xf19d66e82ffe8e203b30df9e81359f8a201517adDeployed at: Jun 8, 2024 06:16:59 AM UTC
Detected at: Jun 8, 2024 06:17:35 AM UTC
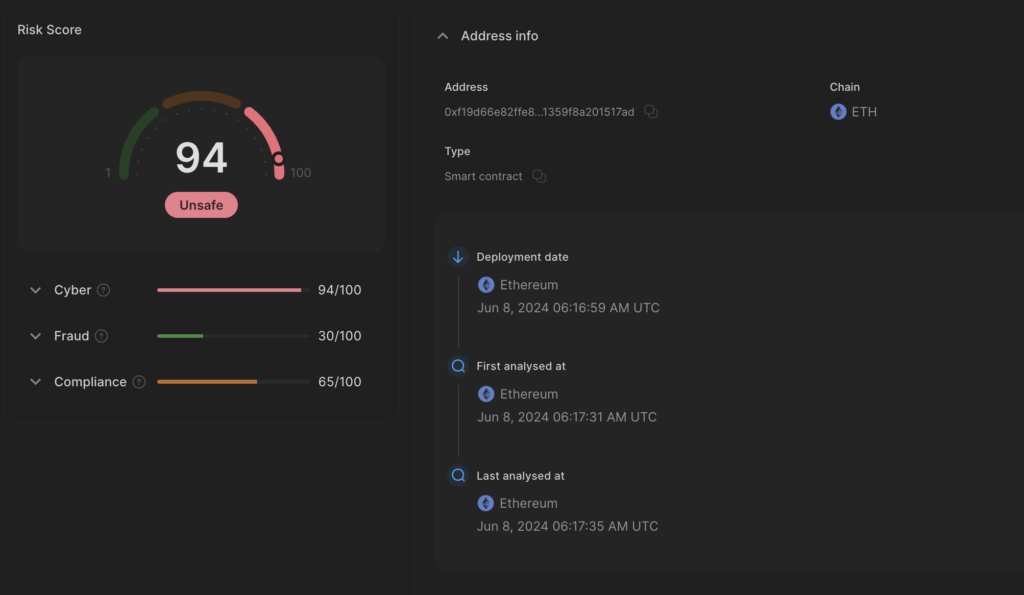
Exploit contract 3
Address: 0x87ed9296bf492ee8807b80923205d8c1fd16f5d8Deployed at: Jun 8, 2024 06:16:59 AM UTC
Detected at: Jun 8, 2024 06:17:34 AM UTC
Exploit contract 4
Address: 0x4cd6feba837b6944be0b2311b7a21036e86c3354Deployed at: Jun 8, 2024 06:28:47 AM UTC
Detected at: Jun 8, 2024 06:29:04 AM UTC
Trigger contract
Address: 0x21c58d8f816578b1193aef4683e8c64405a4312eEmpty contract, just used for triggering the exploit from the contract creation code during deployment.
Victim contract
Proxy address: 0x2409af0251dcb89ee3dee572629291f9b087c668Implementation address: 0x05bfa9157e92690b179033ca2f6dd1e86b25ea4dLendingPool contract, part of UwU Lending protocol (Aave V2 fork for lending assets).
The UwU Lend Attack
Phase 1 – UwU Lend Attack setup and flash loans
During the initial phase of the UwU Lend attack, Exploit contract 1 orchestrated nine distinct flash loans from various providers, such as Aave (V2 and V3), Morpho Blue, UniswapV3, Balancer, and Maker. These loans provided the attacker with significant funds, empowering them to execute the following stage of the attack.
Phase 2 – Manipulation
Next, the attacker established a complex loop of borrowing and depositing against the LendingPool contract, manipulating the collateral and debt positions. This involved strategically placing and removing collateral using Exploit contract 2 and 3.
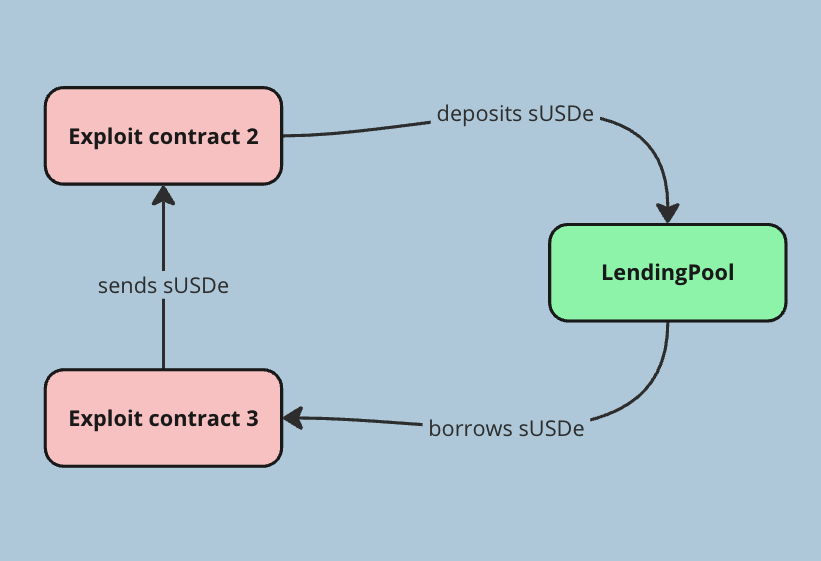
Exploit contract 3 was able to keep borrowing more and more sUSDe, because Exploit contract 2 kept filling back the borrowed assets. This lead to a significant debt for Exploit contract 3 in the LendingPool, resulting in an unhealthy Health Factor for Exploit contract 3’s debt.
During this phase, the attacker manipulated the state of Curve pools, which the LendingPool’s oracle relied on for price calculations. This manipulation caused the price of sUSDe to change from $0.98821237 to $1.03183659.
Phase 3 – Liquidation
In the next step, Exploit contract 2 executed a series of liquidationCalls on the LendingPool contract, liquidating the unhealthy debt created by Exploit contract 3. Due to the higher sUSDe price, Exploit contract 2 was able to pay off the debt of Exploit contract 3 at a much more favourable rate than Exploit contract 3 would have otherwise needed to.
Additionally, Exploit contract 4 borrowed Dai and USDT at the new price.
Phase 4 – UwU Lend Attack Clean-up
Ultimately, all the stolen and borrowed funds during the UwU Lend attack were converted to ETH and transferred to the attacker’s EOA. Notably, the attacker obtained 1946.89 ETH in the initial transaction alone, equivalent to $6.7 million at the time of the hack.
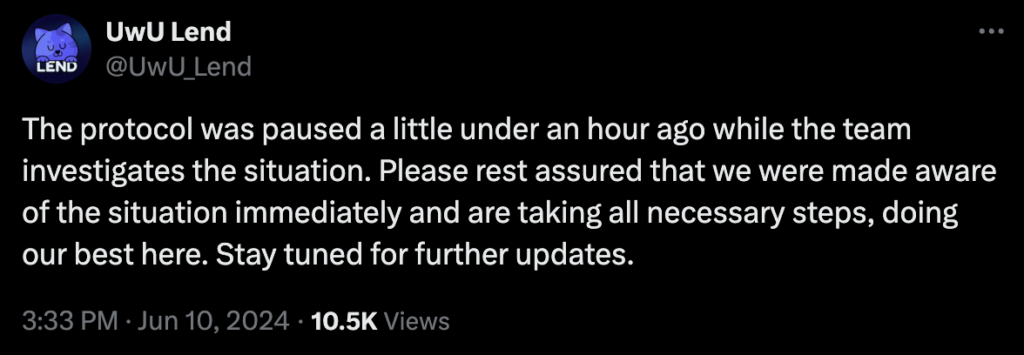
Thankfully, the UwU team was able to manually pause the victim contract approximately an hour after the UwU Lend attack.
Conclusion
This case highlights the undeniable needs for automatic and real-time transaction security in web3.
Audits are an incredibly useful tool to combat exploits, but they are insufficient as fraudsters get increasingly sophisticated. Real-time defenses are necessary, especially if a contract needs to manually be paused. Every second counts. CUBE3.AI is here to level up the security for real-time contract and community defenses. Stop crime before $18 million in losses occur.
With the use of tools like CUBE3’s Runtime Application Self-Protection (RASP), projects and protocols can prevent crime before it happens.
Appendix
1. Malicious transactions
0x242a0fb4fde9de0dc2fd42e8db743cbc197ffa2bf6a036ba0bba303df296408b– $7.15M0xb3f067618ce54bc26a960b660cfc28f9ea0315e2e9a1a855ede1508eb4017376– $6.72M0xca1bbf3b320662c89232006f1ec6624b56242850f07e0f1dadbe4f69ba0d6ac3– $4.14M
2. Funding via Tornado Cash
2.1 Direct Tornado Cash funding
The attacker address received direct funding from Tornado Cash in the following transactions:
0x939b91bbd7ebd0762c9dfd9d667533ada350e16071dd1ef75c2cad094daea16b0xb36e4a35e0e4aef086b8acc6b8ff04b730fe525fcd0a9a40c294209c82fd57fb0x8ef14f4d475a1ab2e45616c2c82aab55a3a3e26ea6b420ccaa1e7c9e9595a4350x9e44d592d3deacfe1d140a797920c6bc059df43791c0a382ba7aeb1347aa27e10xb7ec147843bb881842fb3d30020fb0380d5cfc83cad1f8123359237b90f201b6
2.1 Indirect Tornado Cash funding
Address 0x632E6b5EEC0e52F54Bdd62814D8E242Bc3291ee7 received ~1 ETH from Tornado Cash in transaction 0xb50a8e3b00cd374babf303f36837632128bf5cf86f0696a2434998d451ce6fdc, forwarded to attacker address in transaction 0x1bd71e634dcb794c25f2d49eee13b833a9f51156f19f0f0a5976a4d0eb50a557.

 Einaras Gravrock
Einaras Gravrock
 Sarunas Matulevicius
Sarunas Matulevicius

 Slay Huff
Slay Huff

 Tamás Kelemen
Tamás Kelemen

 Attila Marosi-Bauer
Attila Marosi-Bauer
 CUBE3.AI
CUBE3.AI




















