
Content
$360K Lost to Address Poisoning – CUBE3 Detects It in Real Time
Address poisoning scams are ramping up, and CUBE3 has detected many cases in the past weeks—including a $360K loss just this morning. These scams take advantage of copy-paste habits, tricking users into sending funds to a scammer’s wallet instead of their intended recipient.
What’s critical in cases like this? Speed. Fraud like this happens in seconds, but with real-time detection, businesses can stop funds from being lost before it’s too late.
What Is Address Poisoning?
Address poisoning is a scam where attackers manipulate transaction history to trick users into sending funds to the wrong wallet. There are multiple ways this happens, but the goal is always the same: to create a fake “trusted” transaction history and exploit copy-paste habits.
🔹 Dusting Attack – The attacker sends a small amount (“dust”) to the victim’s wallet from a lookalike address. Later, when the victim copies a past transaction address from an explorer like Etherscan, they accidentally send funds to the scammer.
🔹 0-Allowance Attack (Used in Today’s $360K Case) – Instead of sending dust, the scammer exploits ERC-20 allowances to send a fake transaction in the victim’s name. This is possible because ERC-20 tokens allow transfers with a zero value, meaning a scammer can send tokens on behalf of someone else as long as the transfer amount is zero.
Why This Works: When victims later check their transaction history, they see what looks like a past transfer from their own wallet to the scammer’s address, leading them to copy the wrong address for future transactions.
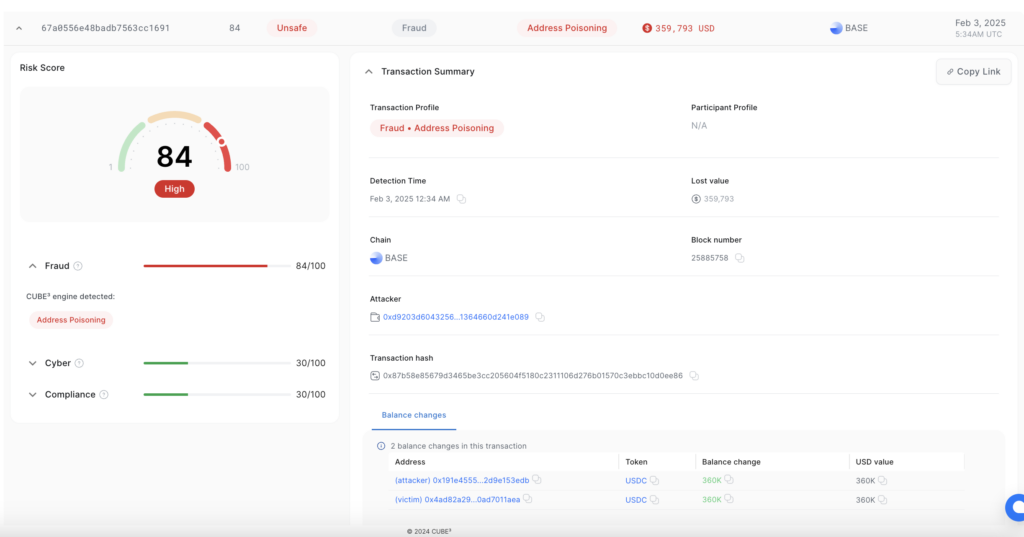
Today’s $360K Address Poisoning Scam
📍 Detected: Feb 3, 2025 – in real time by CUBE3
📍 Lost Value: $360,000 USDC
📍 Chain: Base
📍 Attack Type: Address Poisoning (0-Allowance Attack)
📍 Transaction Hash: 0x87b58e85679d3465be3cc205604f5180c2311106d276b01570c3ebbc10d0ee86
How This Scam Unfolded
1️⃣ The attacker used the 0-allowance method to create a fake outgoing transaction from the victim’s wallet, setting the transfer value to zero.
2️⃣ The transaction appeared in the victim’s history, looking like a legitimate past transfer to the scammer’s address.
3️⃣ When the victim later needed to send funds, they copied this transaction’s address, assuming it was the correct recipient.
4️⃣ $360K was mistakenly sent to the scammer.
🛑 CUBE3 detected this fraud in real time, flagging the poisoned transaction as soon as it occurred. Early detection is critical for businesses and exchanges to warn users and prevent these losses before they happen.
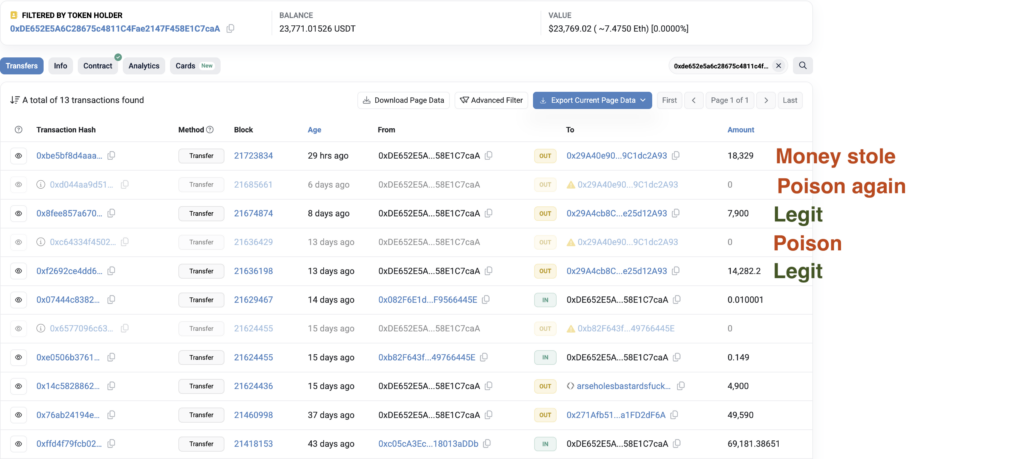
More Address Poisoning Cases Recently
We’ve seen a growing number of address poisoning scams in the past weeks, following similar patterns. In many cases, scammers create multiple poisoned addresses and send small transactions repeatedly to increase the chances of a victim making a mistake. Once the funds are stolen, attackers quickly move them across wallets, making recovery nearly impossible.
How to Protect Yourself from Address Poisoning
✅ Always copy your wallet address from your extension or wallet app. Never copy-paste from a block explorer.
✅ Manually verify the full address before confirming any transaction, especially for large sums.
✅ Be cautious of small unexpected deposits—they could be an attempt to poison your transaction history.
✅ Use real-time fraud detection tools like CUBE3 to catch poisoned transactions before they execute.
Final Thoughts
Address poisoning isn’t a complex hack—it’s a scam that preys on user habits. This is why real-time detection is key to stopping these attacks before funds are lost. Businesses and exchanges need proactive fraud protection to prevent users from falling victim to these increasingly common attacks.
If you’re handling large transactions, take the extra second to verify your recipient address—it could save you thousands.

 CUBE3.AI
CUBE3.AI


 Sarunas Matulevicius
Sarunas Matulevicius

 Tamás Kelemen
Tamás Kelemen

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Einaras Gravrock
Einaras Gravrock




















