
CUBE3 Contributor
$8.5 Million WOOFi Exploit Postmortem Report
1. WOOFi Exploit Background
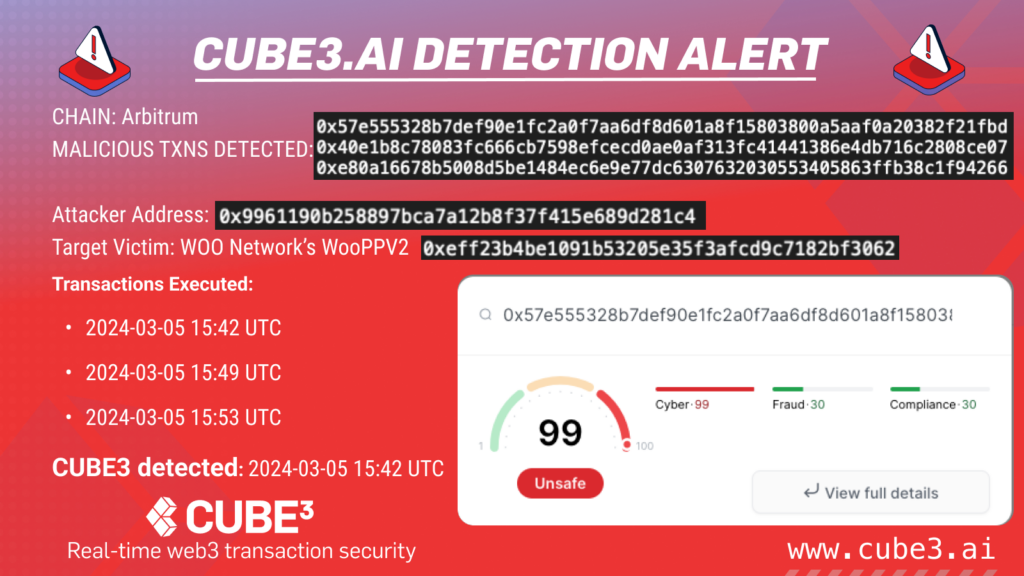
CUBE3 received an alert from Sonar, the transaction security anomaly detector, about a series of transactions targeting WOOFi – amounting to an $8.75M heist.
An example transaction, on the Arbitrum network, was received at 2024-03-05 15:49:29 (UTC):
0x40e1b8c78083fc666cb7598efcecd0ae0af313fc41441386e4db716c2808ce0. The attacker gained $4.4 million USD from this attack.
A detailed analysis can be found below.
2. WOOFi Exploiter / Exploit Addresses
attacker: 0x9961190b258897bca7a12b8f37f415e689d281c4
attacker contract: 0x66634590d7d631e3bf85ef4cd6c89ca7479e22bc
victim: WOO PVV2 –0xeff23b4be1091b53205e35f3afcd9c7182bf3062
3. WOOFi Attack Overview
At the heart of this attack was WOOFi’s Synthetic Proactive Market Making algorithm. This algorithm powers the WOOFi swap by imitating the workings of a CEX order book in a web3 DEX environment.
It does this by getting CEX order book data from an oracle estimating the current mid-price and slippage from the order book depth.
Usually, Uniswap pool price is only determined and affected by the ratio of assets at a given tick. But with WOOFi’s sPMM coming to play. After a swap the PMM contract will try to rebalance prices according to a so-called “reverse sell function”:
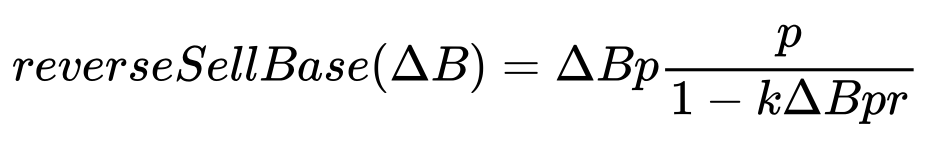
Where p is the average buy price, ∆B is the amount of the base token, and k = slippage/∆Q where ∆Q is the amount of the quote token, and r is the “rebalance” coefficient.
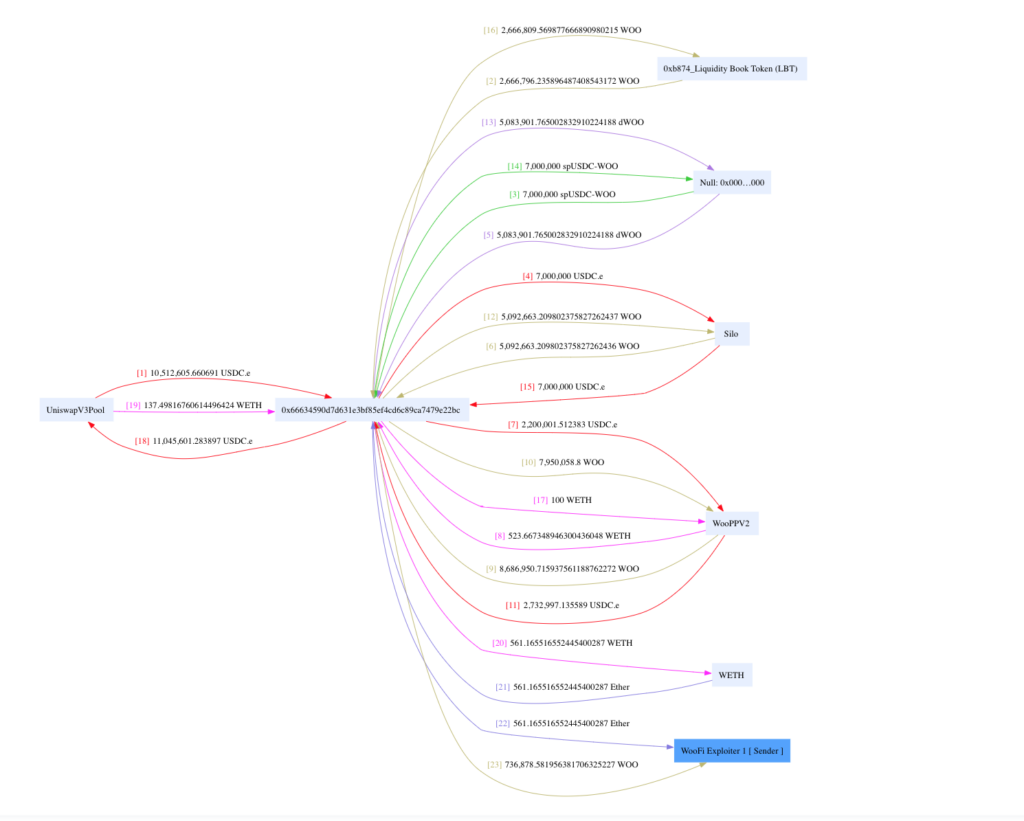
WOOFi Attack Sequence
After an USDC-heavy flashloan from Uniswap, the attacker contract flash loan callback triggers another flashloan from LBT (Liquidity Book Token). The LBT flashloan again, triggers its own callback. Subsequently, that triggers a Silo finance borrow operation that issues the initial WOO tokens to the attacker and its corresponding debt ERC20.
The attacker first dumps $2M USDC onto the WooPPV 2 as a regular ERC20 transaction (not a swap). This updates the contract balance without triggering a WOOFi oracle price update. Next, the attacker swap from USDC to WETH with the same amount that gets ~523WETH
It repeats the same step with a much less initial value of $100k USDC to do the swap against WOO, leaving ~100k tokens. The attacker sends all but this newly swapped tokens to the WOOPPV2 (again, a regular ERC20 transfer) and does the reverse swap against USDC.
Due to the sPMM incorrectly updating the pool price by not accounting for the newly received tokens, the reverse swap for this ~8M WOO results in ~$2M USDC for the attacker.
This time though, as the oracle just witnessed a (relatively) small amount of WOO with $2M of USDC payment, updates the price.
Exploiting this fact, the attacker now can swap the flash-loaned $8M WOO for a minuscule amount ($1.5) USDC. That can be used to repay the Silo loan, and the Uniswap loan when the chain of callbacks return.
An example visualisation of fund flow is shown below:

 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius



 Tamás Kelemen
Tamás Kelemen

 Attila Marosi-Bauer
Attila Marosi-Bauer
 Einaras Gravrock
Einaras Gravrock




















