
Chief Research Officer
Days In Advance, CUBE3 Detected Transit Finance DEX Hacker
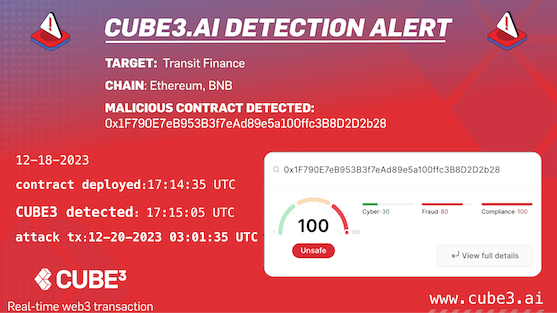
CUBE3 detected another malicious contract, this time days before the Transit Finance DEX hacker executed their exploit. Vulnerabilities we will review in this post and others highlighted previously, are preventable. We encourage web3 projects to use more ML tools that ensure real-time transaction security, like those that CUBE3 has pioneered.
Transit Finance has had its fair share of issues, like the $23 million hack in 2022 (luckily, the majority of funds recovered). A report by SlowMist, concluded:
“The main reason for this attack is that the Transit Swap protocol does not strictly validate the data passed in by the user during token exchange, which results in an arbitrary external call. The attacker exploited this vulnerability in the arbitrary external call to steal tokens that were authorized by users.”
A little over a year later (December 20, 2023), we saw another exploit arise from an attacker taking advantage of a similar inadequate validation vulnerability. Although the amount stolen was not as extreme as 2022, any unforced errors must be defended against in order to reduce continued (and preventable) theft. CUBE3 detected the malicious actor two days before their attack. Unfortunately, Transit Finance was not using the CUBE3 tools and products.
Transit Finance Exploit Basics and Timeline
- December 18, 2023 (15:19:23 UTC) malicious contract deployer address created: 0xf7552ba0eE5BEd0f306658F4A1201f421d703898
- December 18, 2023 (17:14:35 UTC) malicious contract/token “FEE” deployed: 0x1f790e7eb953b3f7ead89e5a100ffc3b8d2d2b28
- December 20, 2023 (03:01:35 UTC) attack transaction executed
- Losses incurred on the following addresses:
- Transit Finance -$67,010.77 USD: 0x00000047bb99ea4d791bb749d970de71ee0b1a34
- Uniswap V3: MUBI -$13,511.67 USD: 0x844eb5c280f38c7462316aad3f338ef9bda62668
Transit Finance Hack Post-Mortem
How did 0xf7…3898 extract almost $100K on December 20th? It all began two days prior…
1. 2023-12-18 17:14:35 UTC – The attacker deployed a malicious contract (token) FEE at 0x1…2b28.
- One item to note within this token, is it has a transfer function…
function transfer(address recipient, uint256 amount) public payable {
require(4 + (msg.data.length - 4) - 4 >= 64);
0x564(amount, recipient, msg.sender);
return True;
}- 🚩 However, the clever function only works when the transaction is initialized/started by the attacker’s address. 🚩
function 0x564(uint256 varg0, address varg1, address varg2) private {
require(address(tx.origin) == address(0xf7552ba0ee5bed0f306658f4a1201f421d703898));
v0 = _SafeSub(_balanceOf[varg2], varg0);
_balanceOf[varg2] = v0;
require(_balanceOf[varg1] <= _balanceOf[varg1] + varg0, Panic(17)); // arithmetic overflow or underflow
_balanceOf[varg1] = _balanceOf[varg1] + varg0;
return ;
}- 2023-12-19 0:51:23 UTC – Then, they created a liquidity pool for the token on Uniswap and added a small amount of liquidity to it.
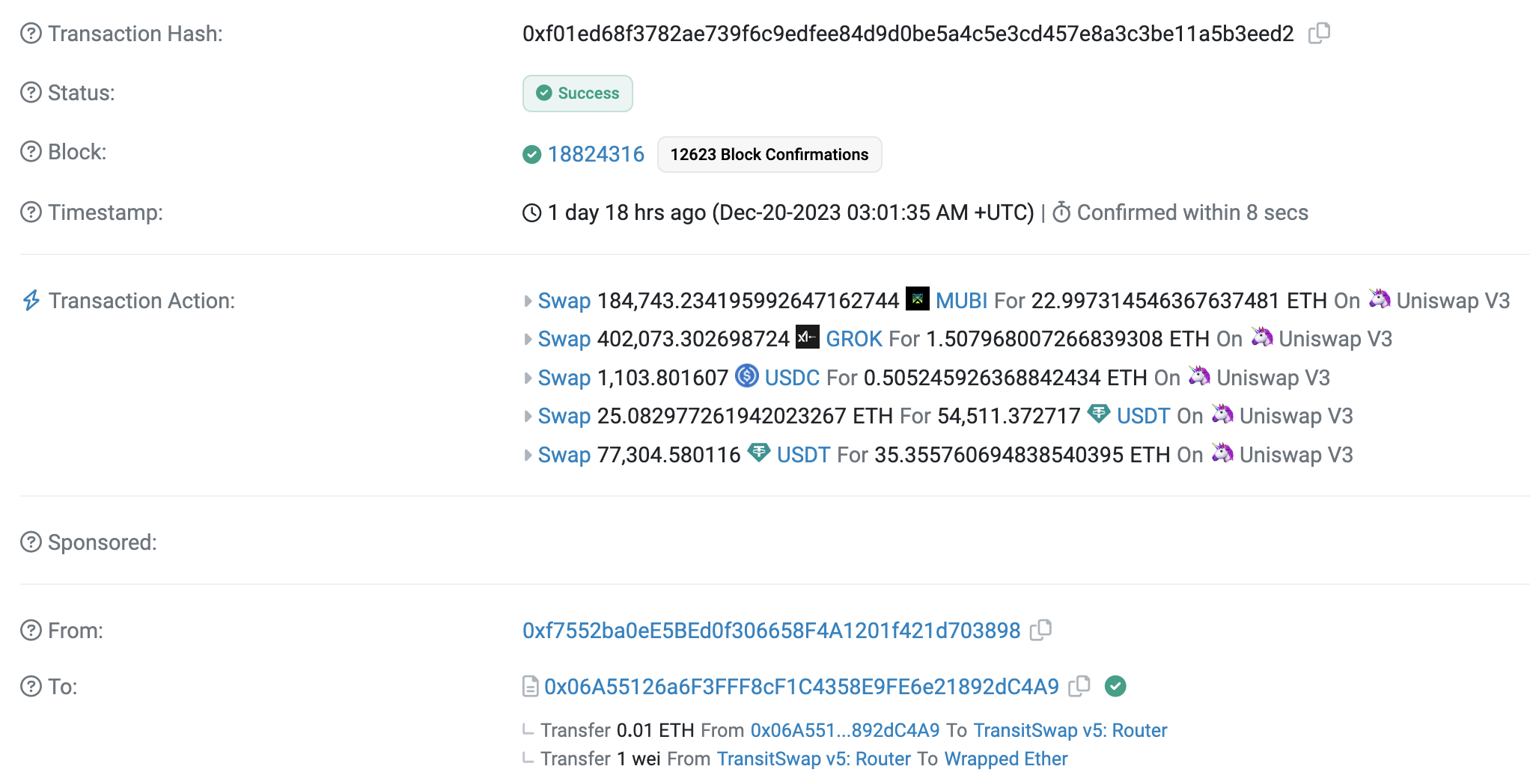
- 2023-12-20 03:01:35 UTC – A few hours later, the attacker tricked Transit Finance “exactInputV3Swap” function, resulting in the following losses:
- 0x0…b1a34 (TransitFinance) = -$67,010.77 USD
- 0x8…2668 (Uniswap V3: MUBI) = -$13,511.67 USD
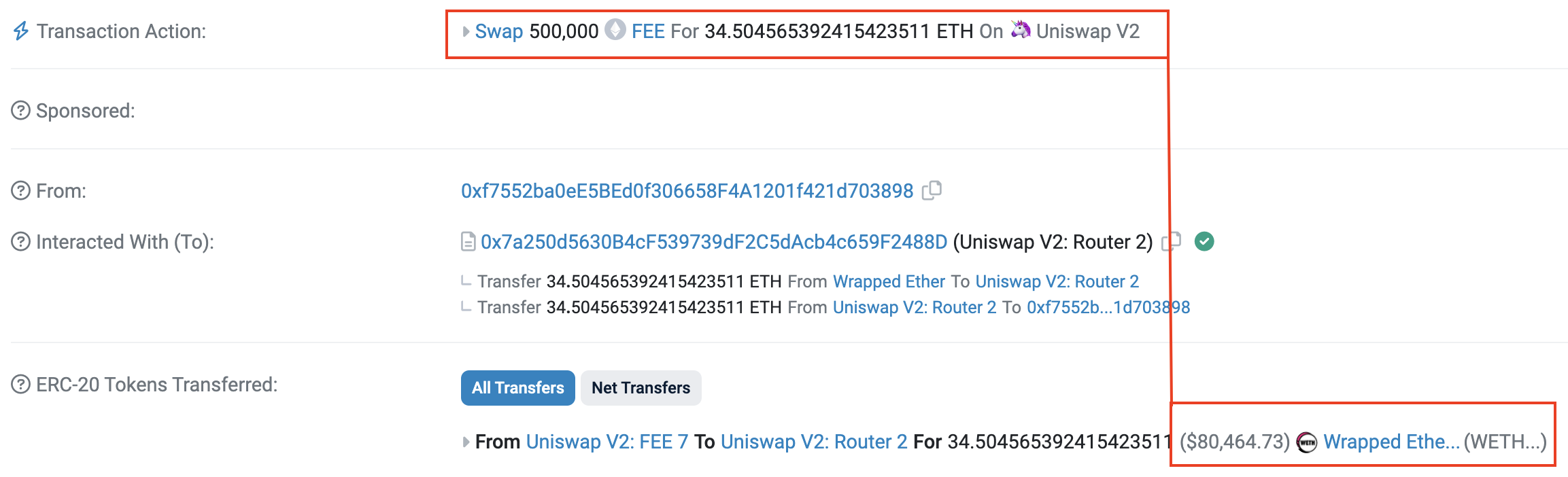
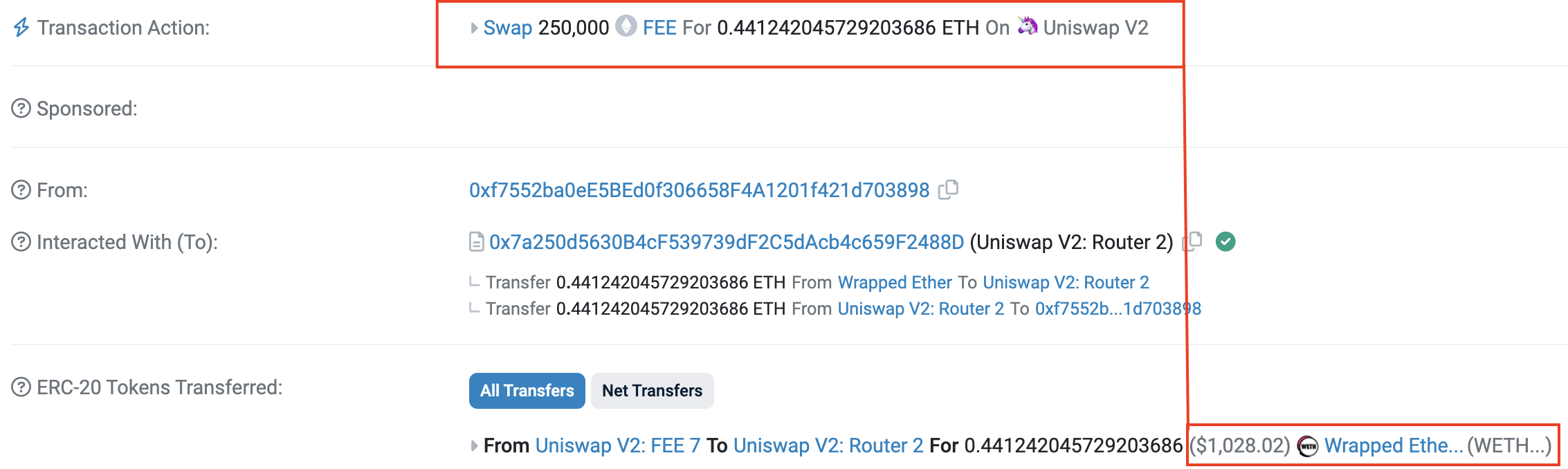
- The next step was two swap transactions of the malicious token “FEE” for ETH:
- After the swap, $80K USD in liquidity was sent to the pool. The attacker gained a profit by selling tokens to the pool, which had just been boosted with stolen money.
CUBE3 Detection Timeline
An interesting element of this hack is that it initially started on BNB and then moved to Ethereum. The addresses used were the same on both chains. CUBE3 does not differentiate between addresses on different chains; if someone is acting maliciously, they are treated as such on all chains.
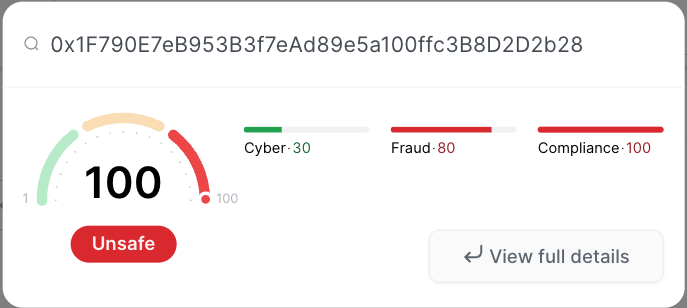
For 0x1…2b28 contract address, you can see the timeline of CUBE3 detection:
- [Binance chain] 2023-12-18 (17:06:20 UTC) – Address funded from Tornado Cash
- [Ethereum chain] 2023-12-18 (17:15:05 UTC) – ML malicious contract detected on deployment
- [Ethereum chain] 2023-12-18 (17:16:32) – Address funded from Tornado Cash
CUBE3 initially flagged this address when it received funds from Tornado on BNB. From that point, CUBE3 was on alert. CUBE3 flagged the activity again when the money moved to Ethereum and when the malicious contract was deployed on December 18th, 17:15:05 UTC.
Protect Your Contracts Before It’s Too Late
By exploiting Transit Finance multiple times, hackers expose the weaknesses of even well-established DeFi projects, demanding immediate action to bolster security. Although the stolen sum this time is less compared to 2022, it underscores a persistent problem – preventable losses due to inadequate security measures.
This is why CUBE3 was created. Our real-time transaction protection tools, pioneered in the field of ML-powered security, could have prevented this attack altogether. CUBE3 detected the malicious contract two days before the attack even occurred, raising red flags about its suspicious activity.
Imagine the peace of mind knowing your contracts are protected 24/7 by the best in class AI efficacy, constantly on the lookout for deceptive threats. CUBE3 doesn’t just identify vulnerabilities; it provides actionable insights and proactive countermeasures to stop attacks before they occur.
Don’t wait for your project to become the next headline. Take control of your security today. Sign up for free and integrate CUBE3’s advanced tools into your workflow.
Protect web3 with the confidence of real-time transaction protection.

 Einaras Gravrock
Einaras Gravrock


 Attila Marosi-Bauer
Attila Marosi-Bauer
 Sarunas Matulevicius
Sarunas Matulevicius

 CUBE3.AI
CUBE3.AI


 Tamás Kelemen
Tamás Kelemen



















