Chief Research Officer
Multi-Vector Transaction Attack Postmortem: Channels Finance
On January 31, 2024 at 9:10 PM +UTC, CUBE3 received an alert from our AI anomaly detector about a multi-vector transaction attack on the Arbitrum network.
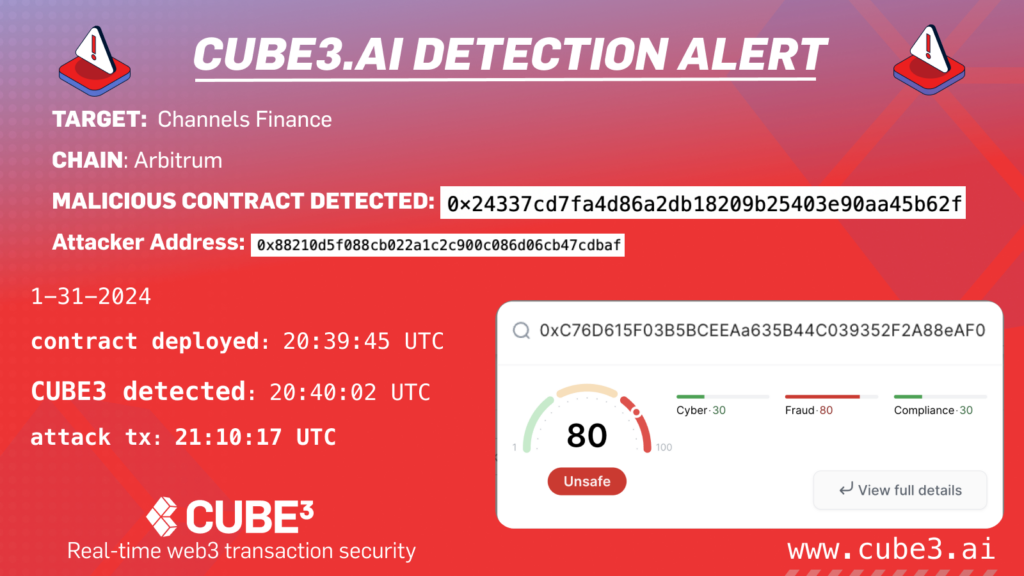
The attacker gained $5,100US, which we’ve analyzed in detail below. Although the wider web3 ecosystem may not find this amount impactful, CUBE3 can block exploits of any size. More importantly, this was an exploit that used multiple types of attack vectors from precision errors, malicious interface callbacks and flash-loan amplifications. It’s important to examine and share these attack vectors, as this may be a test for a larger exploit, which Channels Finance is unfortunately familiar with…
Just last month, CUBE3.AI detected a $250K loss from Channels Finance on BSC network to start 2024:
CUBE3 monitors, detects and blocks exploits on multiple chains, today we are reviewing another Channels exploit, this time on Arbitrum.
Let’s dive in…
Background
- Attacker Contract: `0x88210d5f088cb022a1c2c900c086d06cb47cdbaf`
- Victim: channels usd – `0x5447ab7e7987af871f6558b6398529806ef21eaf`
- Attacker borrower: `0x24337cd7fa4d86a2db18209b25403e90aa45b62f`
- Drainer contract: `0x60ccca913555950f8d15a4035ffa3f302a02cc86`
A Multi-level Heist
In the first step of the attack, our crook gets a flashloan in WETH and Bridged USDC to a contract that has a special `receiveFlashLoan` hook.
Upon receiving the tokens, the hook deposits these tokens into the respective SushiSwap pool `0x905dfcd5649217c42684f23958568e533c711aa3`.
Then, in the same call, borrows $5,140 USDT from channels USD (0x92f6aa3d3d4b46f5e99a26984b4112c7faa0c96c) which the attacker will (mostly) drain with another contract deployed inside the flashloan hook.
The new contract initiates a series of cSLP mint & redeem cycles that exploit a discrepancy in the calculation of`redeemAmount` and `redeemTokens` during `redeemUnderlying` that stems from a precision error.
For example, in the first `mint` call, it carefully makes the mint amount to be slightly above the stored exchange rate:
{
"msg.sender":"0x60ccca913555950f8d15a4035ffa3f302a02cc86",
"func":"exchangeRateStored",
"args":[],
"return":{
"out0":"50000014146011909090909090909090"
}
}
{
"msg.sender":"0x60ccca913555950f8d15a4035ffa3f302a02cc86",
"func":"mint",
"args":{
"amount":"50000014146012"
},
"return":{
"out0":false
}
}
{
"msg.sender":"0x60ccca913555950f8d15a4035ffa3f302a02cc86",
"args":{
"redeemAmount":"100000028292022"
},
"return":{
"out0":"0"
}
}(100000028292022 / 2) – 50000014146012 = -1 which is our potentially maliciously gained token.
But we need to verify in the cUSD code whether “redeemToken” does not correspond to this last token. There are also cases where the difference is slightly larger.
The total extra SLP the attacker gains from this drain cycle is `(606137794435308 – 56137978814419) / 1e18= 0.000549999815620889`, which corresponds to 2.3% of the total supply at the time of the attack.
With access to these extra tokens, the attacker sends it back to the original SLP pool and gets extra USDT valuing their cash borrow at Channels in exchange for the gratis tokens, and pays back the flash loan in full.
Conclusion
We see that this is a complex multi-vector transaction attack combining various techniques ranging from precision errors, malicious interface callbacks and flash-loan amplifications, which would be very hard to even detect without sophisticated heuristic scanners.
That’s why CUBE3 ML is another critical tool in your web3 layered security strategy.
Special thanks to Silur for investigation support and contributions to this article.
Why CUBE3?
CUBE3 is here to ensure your projects are safe and secure post-launch.
Stay safe web3! DON’T GET REKT.

 Tamás Kelemen
Tamás Kelemen
 Einaras Gravrock
Einaras Gravrock

 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius

 Attila Marosi-Bauer
Attila Marosi-Bauer