
CUBE3.AI Security Researcher
$28M Penpie Exploit Detected Within Seconds by CUBE3.AI
In a swift attack on Penpie, a hacker facilitated the theft of $28M across Ethereum and Arbitrum by using a flash loan from Balancer. CUBE3.AI’s models detected the exploit contract merely 32 seconds after deployment, and 10 minutes before the first malicious transaction, highlighting the need for real-time security measures in the web3 space.
Key Details:
- Chain: Ethereum, Arbitrum
- Total loss: $28 million
- Attacker Address: 0x7a2f4d625fb21f5e51562ce8dc2e722e12a61d1b (Ethereum & Arbitrum)
- Exploit Contract: 0xcde2cd6aeaaf0238f4ce33295be13704e4a97de2 (Ethereum)
- Flash Loan Provider: Balancer
- Victim: Penpie
The Attack
On Sep 3, 2024, CUBE3.AI’s detection system flagged a contract created by the attacker. Just 10 minutes later, the first malicious transaction drained a significant portion of funds. Here’s a breakdown of the malicious transactions:
- Ethereum
- Transaction Hash: 0x56e09abb35ff12271fdb38ff8a23e4d4a7396844426a94c4d3af2e8b7a0a2813
- Loss: $16.35M
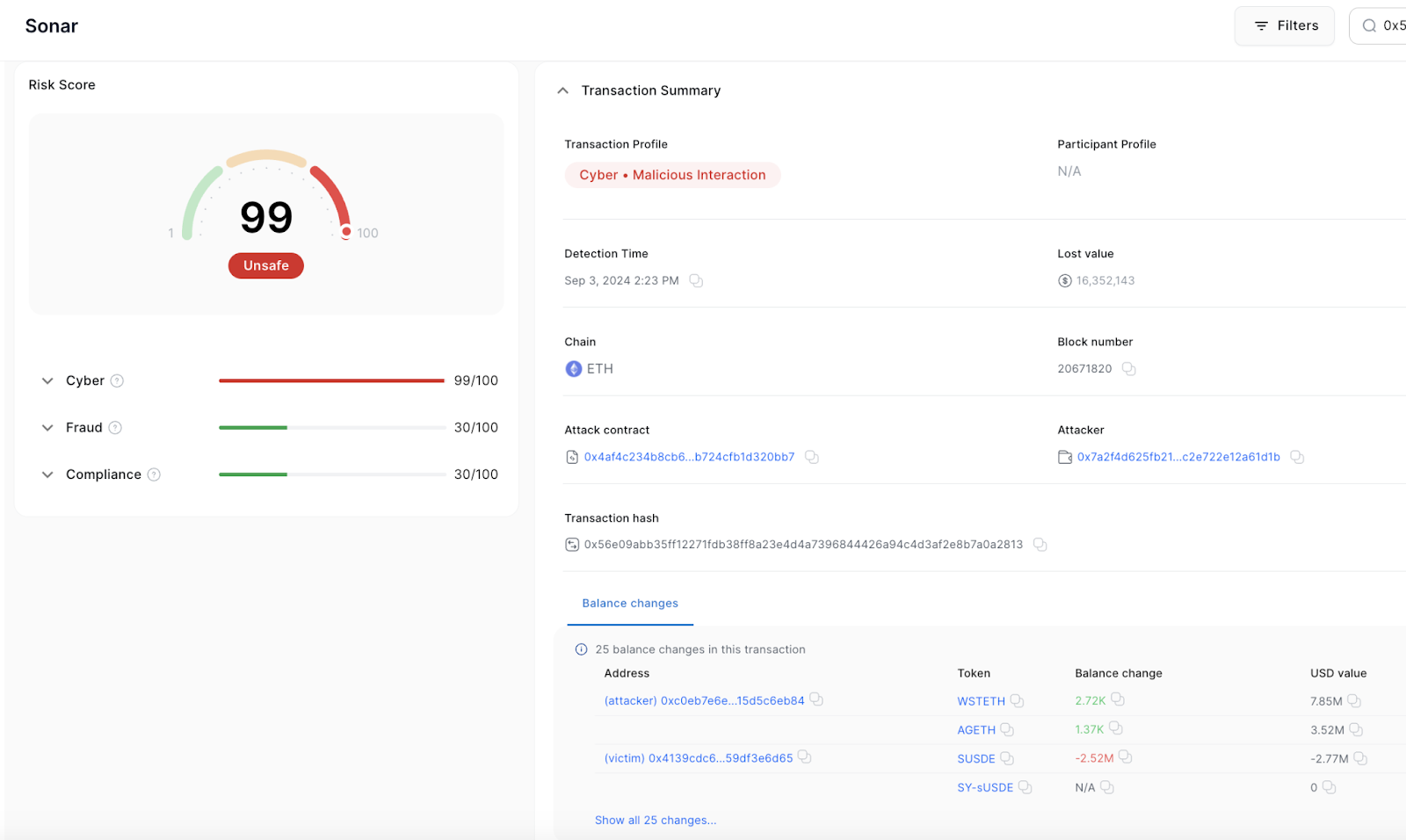
- Ethereum
- Transaction Hash: 0x42b2ec27c732100dd9037c76da415e10329ea41598de453bb0c0c9ea7ce0d8e5
- Loss: $5.74M
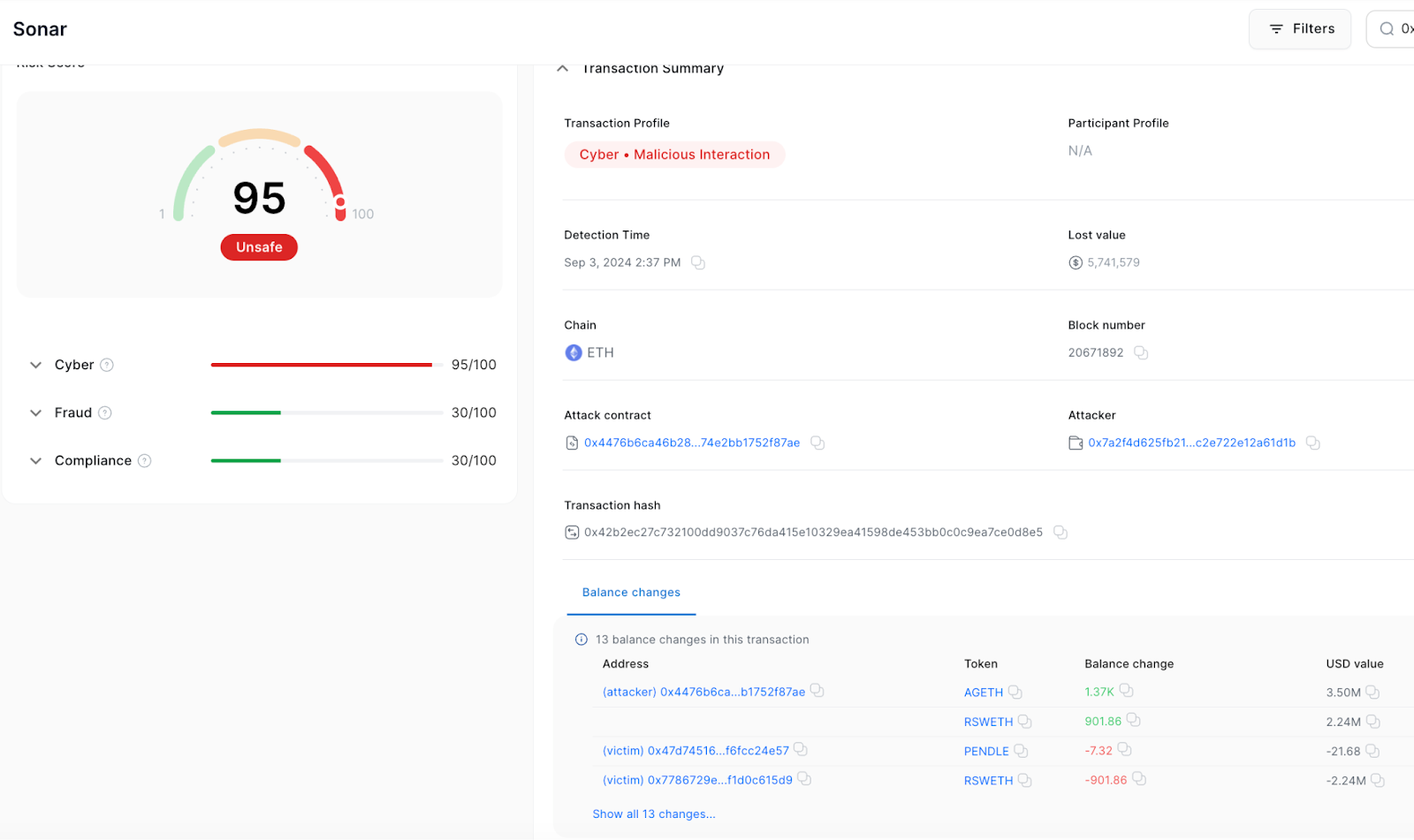
- Ethereum
- Transaction Hash: 0x663b55a1ee992603f7636ef23ff5cf19d3b261ab81494d06e218c86482df5342
- Loss: $5.44M
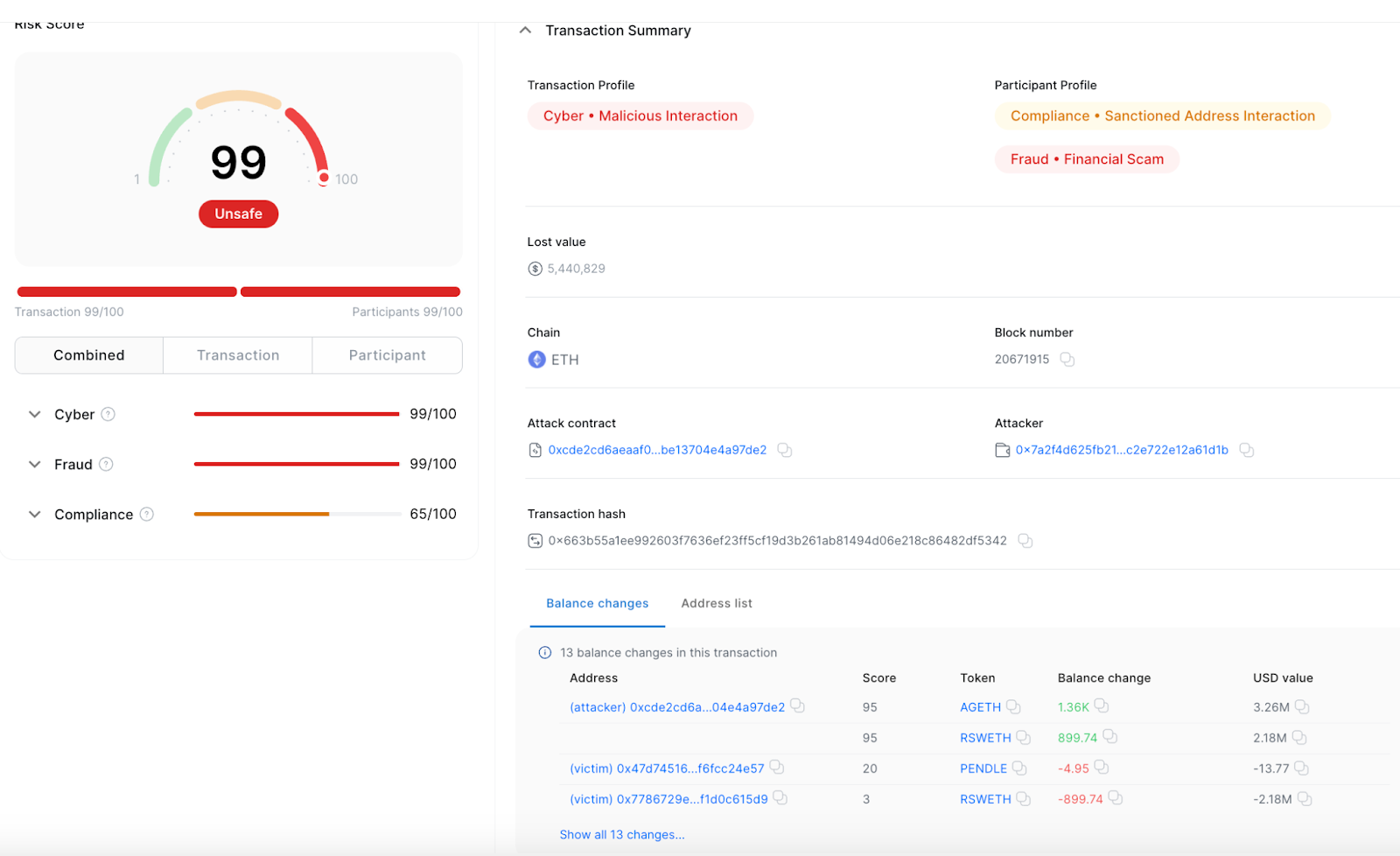
- Arbitrum
- Transaction Hash: 0x67c5400da117b906f8c0fc5f5149e4ea10ed6358cd9ea2ec0ed8f559d757b7df
- Loss: $678K
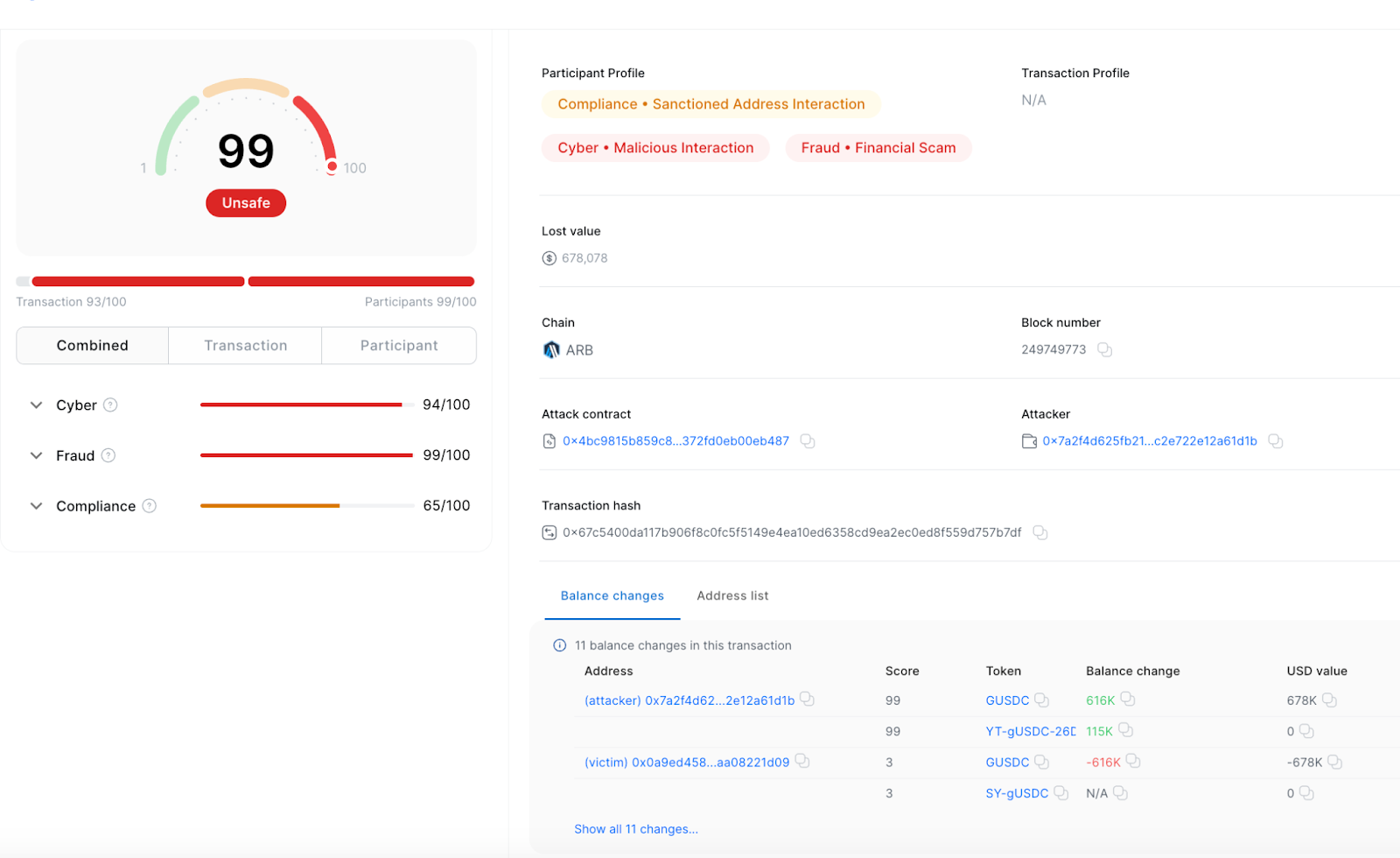
These transactions resulted in a total loss of $28M across both chains.
Anatomy of the Exploit
The attack exploited a vulnerability in the _harvestBatchMarketRewards internal function in the PendleStaking implementation (0xff51c6b493c1e4df4e491865352353eadff0f9f8), which initiated an external call to another contract. The attacker manipulated this call, redirecting it to the exploit contract, creating a double-spend reentrancy vulnerability.
Leveraging a flash loan from Balancer, the attacker orchestrated a complex exploit across two chains—Ethereum and Arbitrum. With the loaned funds, the attacker executed multiple transactions designed to manipulate the protocol and drain assets from Penpie’s contracts.
Conclusion
Following the attack, the Penpie team responded swiftly by pausing all deposits and withdrawals to prevent further damage and address the exploit. While their quick action is commendable, the need to manually pause smart contracts reveals a vulnerability in many existing security setups.
With CUBE3.AI’s real-time fraud detection, projects like Penpie can avoid the need for such pauses. CUBE3.AI’s Runtime Application Self-Protection (RASP) detects and blocks malicious transactions before they cause damage, preventing the need for emergency measures like halting contract activity.
By leveraging CUBE3.AI’s proactive security solutions, blockchain projects can maintain continuous operations, safeguarding assets and providing uninterrupted service to their users—even in the face of sophisticated attacks.

 Attila Marosi-Bauer
Attila Marosi-Bauer
 CUBE3.AI
CUBE3.AI

 Sarunas Matulevicius
Sarunas Matulevicius


 Einaras Gravrock
Einaras Gravrock




















